For developers striving to build secure APIs, Broken Function Level Authorization (BFLA) is a crucial vulnerability demanding meticulous attention. BFLA belongs to the OWASP API Security Top 10 list and can pave the way to unauthorized access and manipulation of functionality within your API, compromising the overall integrity of your system. This occurs when applications lack adequate authorization checks focused on specific functions or features. This weakness enables attackers to manipulate calls to endpoints to which they shouldn't have access, potentially escalating access to functions reserved for higher privilege levels (like administrative actions).
Let's explore BFLA in more detail, including its nature, common root causes, and how to pinpoint BFLA vulnerabilities in your API code. Following this, we'll use StackHawk to scan a susceptible Flask application, locate a BFLA vulnerability in one of our endpoints, and then implement the necessary fix. Finally, we'll re-scan to validate that the vulnerability has been patched. Let’s begin by digging into the foundations of BFLA vulnerabilities.
What is Broken Function Level Authorization (BFLA)?
Broken Function Level Authorization (BFLA) remains a significant risk to the security of APIs. This vulnerability surfaces when an API fails to implement robust controls, allowing users to access features and functions beyond their assigned permissions. Function-level authorization defines specific API actions that different user groups (or roles) can execute. For instance, a regular user of a banking app should not be able to perform administrative actions related to other user accounts. BFLA flaws emerge when these intended restrictions are weak or missing.
The pattern of BFLA attacks is straightforward. An attacker begins by analyzing API behavior to understand how API endpoints are named or structured. Then, they might attempt to alter HTTP methods (e.g., switch from GET to POST) or other elements in the function call requests. This is done in the hope of reaching unauthorized functionality. Weak authorization checks allow attackers to view, change, or execute commands with elevated privileges.
How Does BFLA Differ from BOLA?
You might encounter terms like "BFLA" and "BOLA" (Broken Object Level Authorization) in API security discussions. The overlap between these terms is significant, so understanding the subtle distinction is helpful. BOLA spotlights scenarios where an API directly exposes references or identifiers to internal objects, making them vulnerable to manipulation. BFLA takes a broader view, focusing on any breakdown in the logic that enforces function-level authorization within an API.
In short, BFLA is the broader category that encompasses BOLA-type issues. BFLA concerns go beyond the use of predictable IDs; they also stem from a failure to rigorously validate whether the user making a request is authorized to execute that particular API function.
What is The Root Cause of BFLA?
BFLA vulnerabilities typically stem from development practices that prioritize convenience over robust authorization. Here are several common contributing factors:
Oversimplification of Authorization: APIs that rely on basic checks without considering the full range of functions they expose are vulnerable to exploitation.
Lack of Consistent Authorization: Inconsistent or absent authorization across various API endpoints creates potential entry points for attackers.
Blind Trust in User-Supplied Data: All information users provide must be treated cautiously and validated, including parameters that might influence the accessed functionality.
"Security Through Obscurity": Relying on hard-to-guess API paths or obscure naming conventions offers a false sense of security. Determined attackers can often bypass these.
At its core, BFLA arises from the absence of robust and function-specific authorization controls embedded directly into the API's design.
Preventing Broken Function Level Authorization (BFLA) Vulnerabilities
The key to avoiding BFLA vulnerabilities lies in adopting a comprehensive approach encompassing secure design, robust authorization, and continuous monitoring. Here are some best practices:
Enforce Rigorous Authorization Checks: Validate users' permissions with each attempted access to an API function.
Least Privilege Principle: Limit user and application access to the minimum necessary functions and data required.
Input Validation: Carefully scrutinize all input data from users, particularly values that can influence what API functions are accessed.
Regular Security Testing: Automate security testing tools like StackHawk and employ penetration testing to uncover vulnerabilities like BLFA proactively.
Developer Education: Train your development team in secure coding practices with awareness of BFLA and similar vulnerabilities.
By following these guidelines, you'll significantly reduce your application's risk of BFLA vulnerabilities, ensuring users can only access what they're supposed to. Now, let’s put this into practice by looking at a vulnerable Flask application and using StackHawk to identify the BFLA vulnerability and help us verify that the fix we will implement successfully remediates the issue.
Detecting and Fixing BFLA Vulnerabilities in Flask (Python)
Building The Vulnerable Endpoint
Below is an example of a simple Flask API with a BFLA vulnerability. This API allows users to delete a user based on a user ID in the URL. However, it doesn't perform any checks to ensure that the user making the request has the applicable role, being an “admin, before running the logic within the endpoint. This demonstrates a BFLA vulnerability in its simplest form, allowing an unauthorized user to perform a function they shouldn’t have access to.
Please note: This is an intentionally vulnerable API for demonstration purposes. Do not use this code in an actual application, as it is not production-ready.
First, create a new directory for your project and navigate into it. If you do this through a terminal, you can run the command below.
mkdir bfla-api-examplecd bfla-api-exampleNext, with the terminal, point to the root directory and initialize a new Python project/virtual environment using the following command.
python3 -m venv venvsource venv/bin/activateFinally, before we write any code, we will install the following dependencies:
Flask: for setting up the server.
Flask_SQLAlchemy: for ORM support.
Flask_RESTx: for generating OpenAPI specs and other REST functionalities
To do this, using the same terminal pointed to the project root, run the following:
pip install Flask Flask_SQLAlchemy flask-restxNow, we will begin to create our API application. In the root directory of the project, create a file named app.py. This file will contain your Flask server and the API endpoint, including the BFLA vulnerability.
After creating and opening the app.py file, add the following code
from flask import Flask, jsonify, request
from flask_sqlalchemy import SQLAlchemy
from sqlalchemy.sql import text
from flask_restx import Api, Resource, fields
app = Flask(__name__)
app.config['SQLALCHEMY_DATABASE_URI'] = 'sqlite:////Users/matttanner/Documents/GitHub/bfla-api-example/test.db'
app.config['SQLALCHEMY_TRACK_MODIFICATIONS'] = False
db = SQLAlchemy(app)
api = Api(app, version='1.0', title='User API', description='A simple User API with a BFLA vulnerability')
ns = api.namespace('users', description='User operations')
user_model = api.model('User', {
'id': fields.Integer(readOnly=True, description='The user unique identifier'),
'name': fields.String(required=False, description='The user name'),
'role': fields.String(required=False, description='The user role')
})
class User(db.Model):
__tablename__ = 'users'
id = db.Column(db.Integer, primary_key=True)
name = db.Column(db.String(50))
role = db.Column(db.String(50))
def insert_example_users():
if User.query.count() == 0:
# Only insert if the table is empty to avoid duplicate entries on reload
db.session.add(User(id=1, name="John Doe", role="admin"))
db.session.add(User(id=2, name="Jane Smith", role="user"))
db.session.add(User(id=3, name="Alice Johnson", role="user"))
db.session.commit()
@ns.route('/<int:id>', methods=['GET', 'PUT'])
@ns.response(404, 'User not found')
@ns.param('id', 'The user identifier')
class UserResource(Resource):
@ns.doc('get_user')
@ns.marshal_with(user_model)
def get(self, id):
"""Fetch a user given its identifier"""
try:
# Use parameterized SQL query to prevent SQL injection
query = text("SELECT * FROM users WHERE id = :id")
# Execute the query with safe parameter substitution
result = db.session.execute(query, {'id': id})
user = result.fetchone()
if user:
return user
else:
api.abort(404)
except Exception as e:
# Handle the exception here
print(f"An error occurred: {str(e)}")
api.abort(500, f"An error occurred: {str(e)}")
@ns.doc('update_user', include=False)
@ns.marshal_with(user_model)
def put(self, id):
"""Update a user given its identifier"""
try:
# Use parameterized SQL query to prevent SQL injection
query = text("UPDATE users SET name = :name, role = :role WHERE id = :id")
data = request.get_json(silent=True)
# Check if request body exists
if data:
# Execute the query with safe parameter substitution
db.session.execute(query, {'id': id, 'name': data['name'], 'role': data['role']})
db.session.commit()
return User.query.get(id)
except Exception as e:
# Handle the exception here
print(f"An error occurred: {str(e)}")
api.abort(500, f"An error occurred: {str(e)}")
# Serve the OpenAPI spec at /api-spec/
@app.route('/api-spec/')
def api_spec():
# Manually remove the PUT endpoint documentation
if '/users/{id}' in api.__schema__['paths']:
if 'put' in api.__schema__['paths']['/users/{id}']:
del api.__schema__['paths']['/users/{id}']['put']
# Set the server URL
api.__schema__['basePath'] = 'http://localhost:4000'
return jsonify(api.__schema__)
if __name__ == '__main__':
with app.app_context():
db.create_all()
insert_example_users()
app.run(debug=True, port=4000)
Let's run through a quick breakdown of the updated code, which demonstrates how to create a simple web server using Flask, Flask-SQLAlchemy for database interactions, and Flask-RESTx for building REST APIs with built-in OpenAPI (Swagger) documentation. The code provides a REST API for accessing and modifying user information stored in a SQLite database configured for simplicity and demonstration purposes.
1. Initialization of Flask App
app = Flask(__name__) Initializes the Flask application, setting up the basic environment for the API server.
2. Configuration for SQLAlchemy and Database
SQLALCHEMY_DATABASE_URI specifies the database connection, which is a SQLite database located at a specified path on the local filesystem.
SQLALCHEMY_TRACK_MODIFICATIONS sets this variable to False to disable modification tracking to prevent overhead, improving performance since track modifications aren't needed for this example.
3. Database Model Definition
class User(db.Model) defines the database model for users, specifying the table name and columns (id, name, role). This model is essential for interacting with the users table in the SQLite database.
4. Inserting Example Users
insert_example_users() is a function that checks if the user table is empty and populates it with initial data. This is useful for demonstrations and ensures there is data to work with when the API is first run.
5. API and Namespace Configuration
api = Api(...) sets up the Flask-RESTx API manager, which handles the routing and documentation of the RESTful API.
ns = api.namespace(...) defines a namespace for user operations, organizing endpoints under a common path and documentation category.
6. API Endpoint Definitions
The GET Endpoint, defined within UserResource, allows clients to fetch user data by ID. It uses a parameterized SQL query to retrieve data securely, preventing SQL injection.
The PUT Endpoint, also defined within UserResource, allows for updating user data by ID. This method similarly uses parameterized SQL queries for secure database interactions. The include=False parameter in the @ns.doc decorator means that the endpoint will be excluded from automatic API documentation generation, since it is considered a private API for the purposes of this example.
7. OpenAPI Specification Endpoint
@app.route('/api-spec/') serves the generated OpenAPI (Swagger) specification, which provides a machine-readable description of the available API endpoints. The function also manually removes documentation for the PUT method, aligning with its intended restricted access.
8. Server Initialization
The if __name__ == '__main__' block includes commands to initialize the database tables, insert example data, and start the Flask development server on port 4000. This makes the API accessible to clients and ensures that the server starts with the necessary setup completed.
After this code is running, we will have an example Flask app with a SQLite backend for handling simple user data operations. This example shows how to create a basic REST API and how to selectively document API endpoints using OpenAPI specifications, hiding methods from the spec that shouldn’t be publicly available. That being said, there still is a gap regarding the actual authorization of the PUT endpoint meaning that anyone can access the function, and this is where the BFLA vulnerability exists.
Running The Code
Now that our code is complete, it’s time to run the application and bring up our API. To run your API, run the following command in a terminal pointed to the root of your project with your virtual environment still active:
flask run -p 4000Once the application is up and running, you’ll notice that the PUT /user/:id endpoint allows anyone to update user data by specifying a user ID in the URL. This is a straightforward example of a BFLA vulnerability we must remediate.
To demonstrate this, we can issue the following cURL command and see that it works, updating the user without any type of authentication or authorization.
curl --location --request GET 'http://127.0.0.1:4000/users/1' \
--header 'Content-Type: application/json' \
--data '{
"name": "John Doe",
"role": "admin"
}'Detecting The Vulnerability With StackHawk and HawkScan
Now that our code is set up and our API is running, let’s get StackHawk to identify this vulnerability automatically. To do this, you’ll need to ensure you have a StackHawk account. If you need one, you can sign up for a trial account or log into an existing account.
If you’re logging into an existing StackHawk account, from the Applications page, you’ll click Add an App -> Create Custom App.
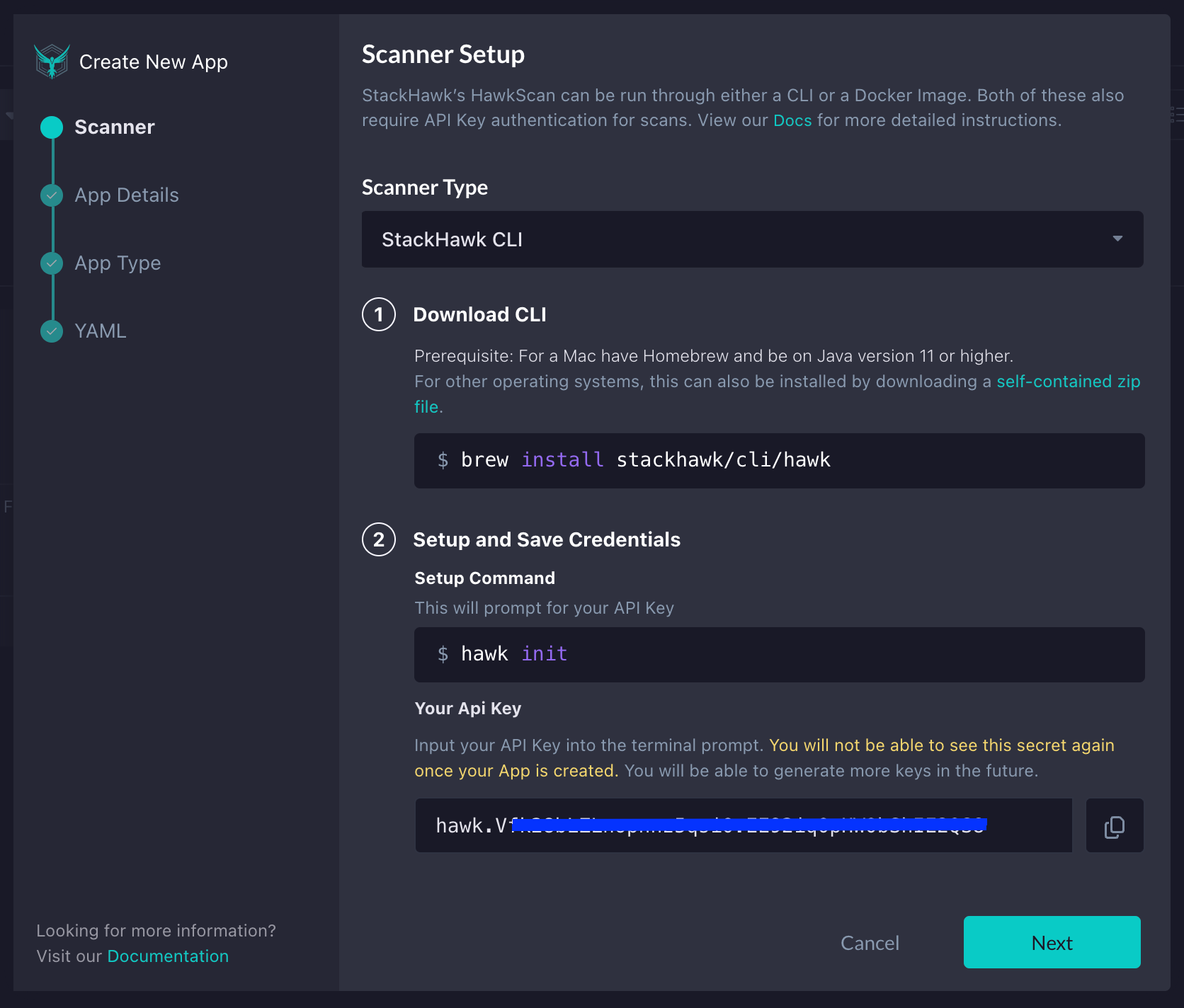
If you’re new to StackHawk, you’ll be automatically brought into the Add an App flow. On the Scanner screen, you’ll see the instructions for installing the StackHawk CLI. Since we will be running our testing locally, we will use this option. Once the hawk init command is executed successfully, click the Next button.
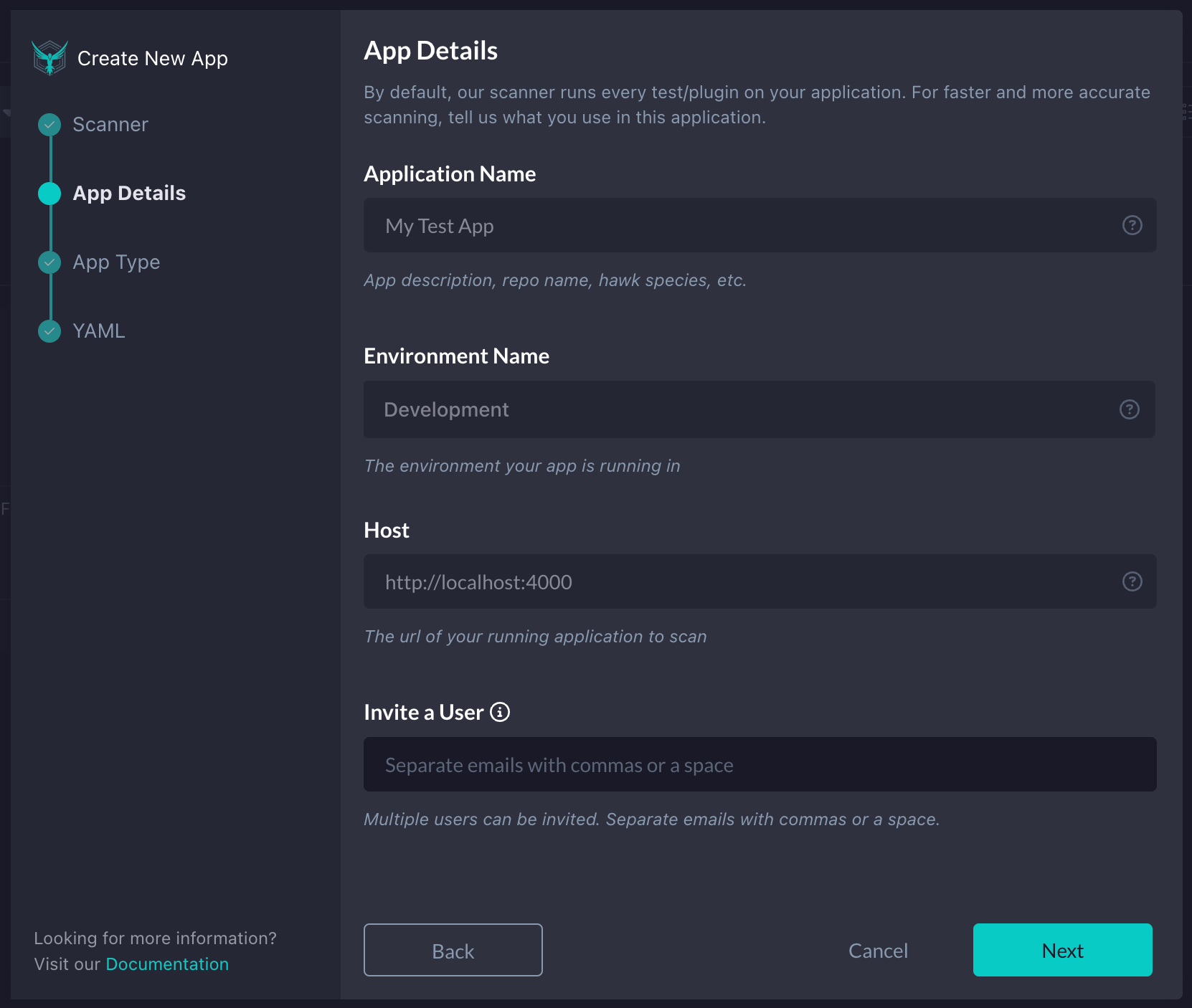
On the next screen, you will fill out an Application Name, Environment Name, and Host. Feel free to copy the default values I’ve added in the screenshot below for our purposes. Once filled out, click Next.
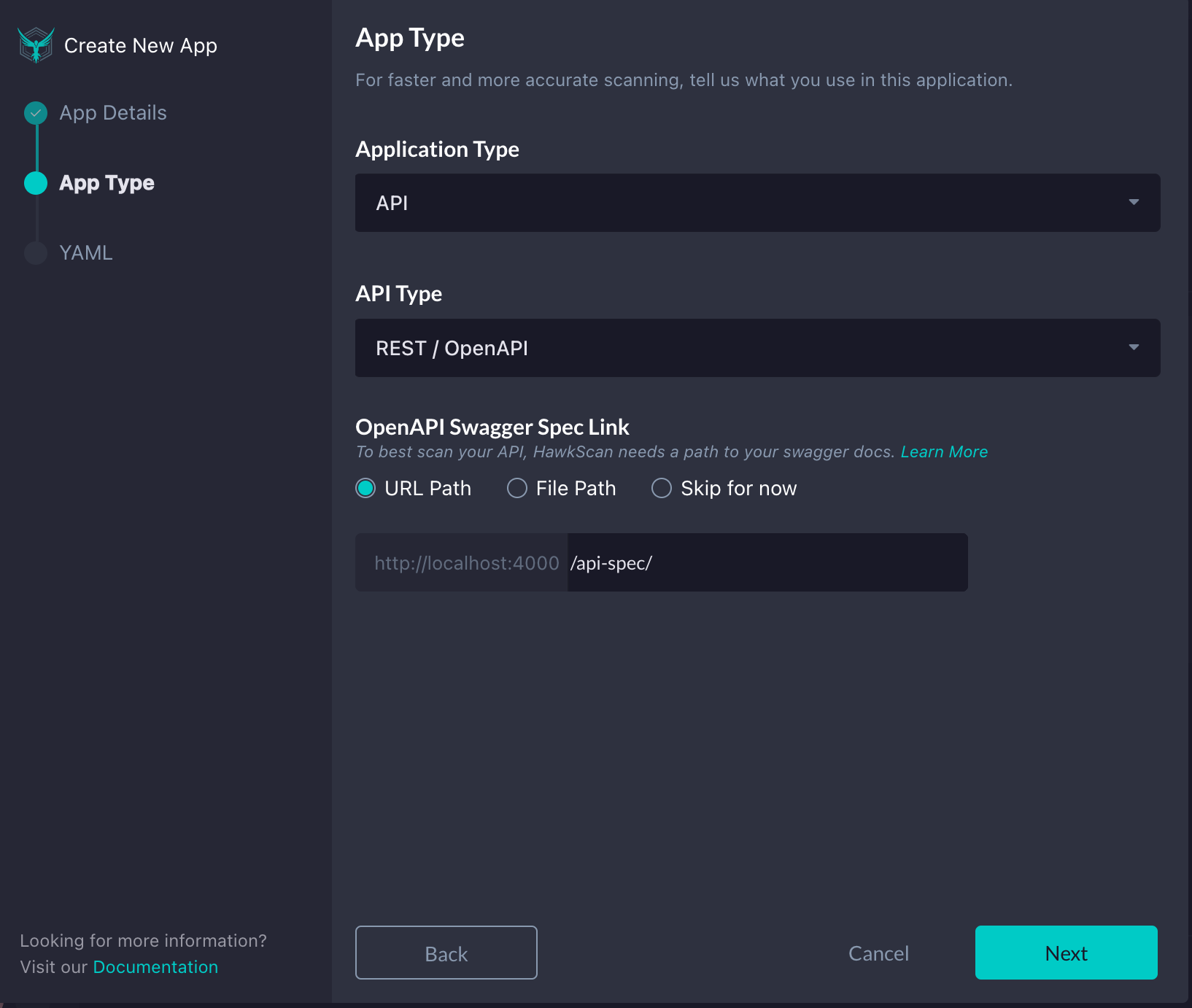
Since we will be testing a RESTful API, on the next page, we will choose our Application Type as “API”, the API Type as “REST / OpenAPI”, and point to our OpenAPI Specification file by selecting URL Path and adding in our endpoint, /api-spec/, into the textbox. Once complete, click Next.
Lastly, we will need to add a stackhawk.yml file to the root of our project. Once the file is added, copy the screen's contents, paste it into the file, and save it. Lastly, we can click the Finish button.
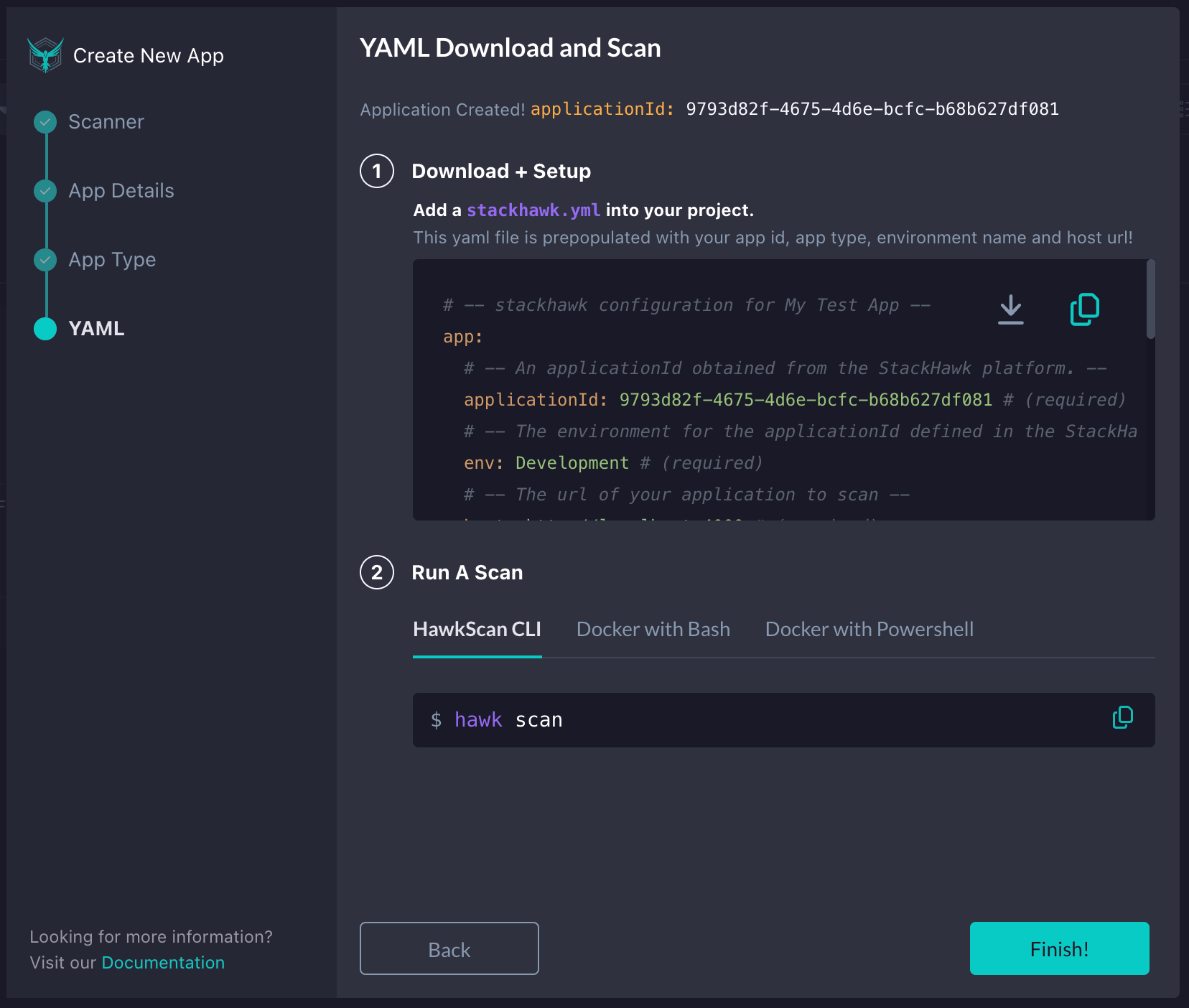
Enabling BFLA Detection in HawkScan
After creating the app in StackHawk, we need to do a few more steps to enable BFLA detection in StackHawk. Two ways to do this are using the "OpenAPI - Experimental" policy or customizing an existing policy. The "OpenAPI - Experimental" policy allows users to scan for the vulnerabilities outlined in the OWASP API Security Top 10.
To set HawkScan up with the "OpenAPI - Experimental" policy, you will log into StackHawk, go to the Applications screen, and click on the settings link for your application.
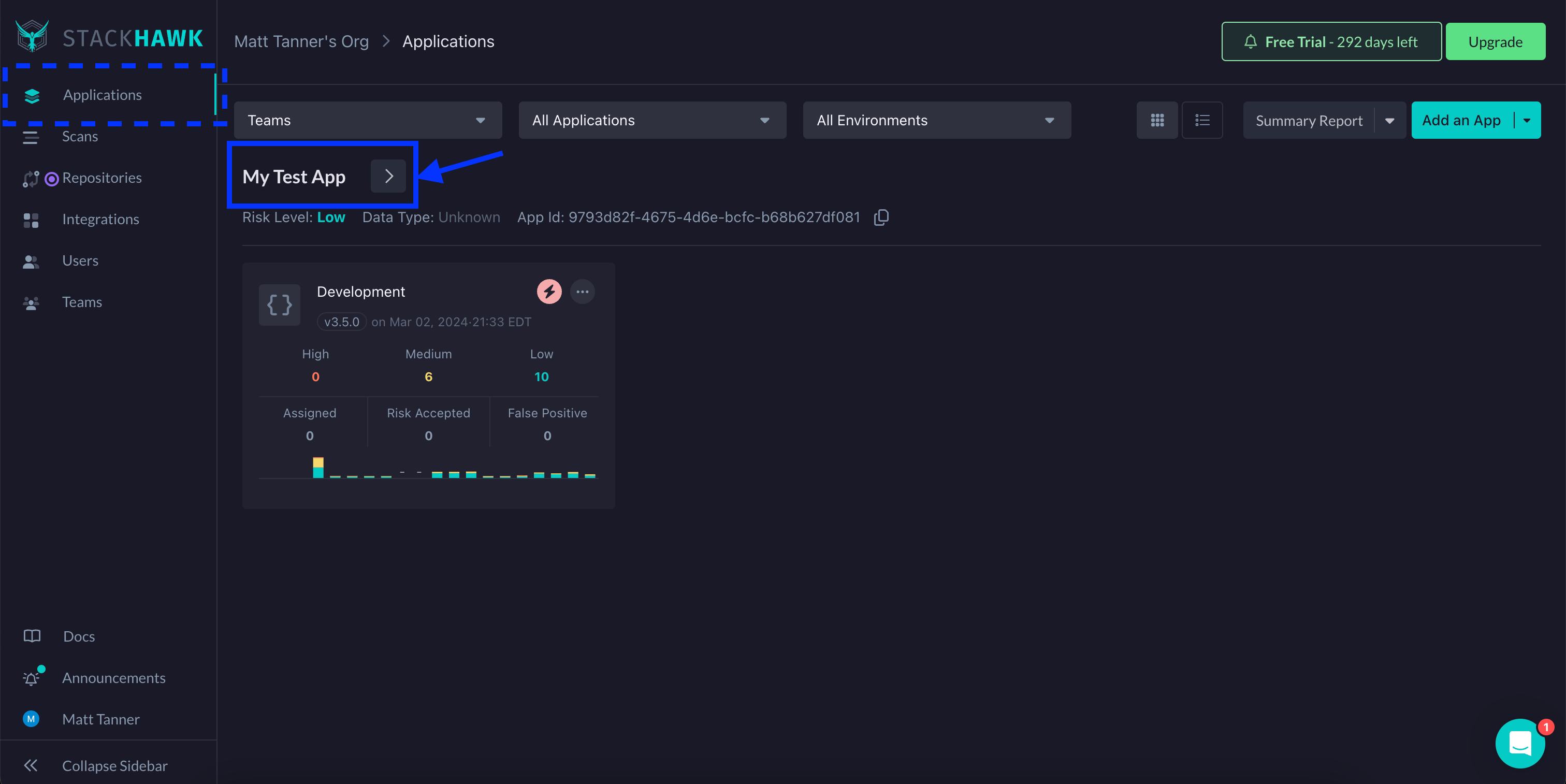
Next, on the Settings screen, under HawkScan Settings, click the Applied Policy dropdown and select the "OpenAPI - Experimental" policy.
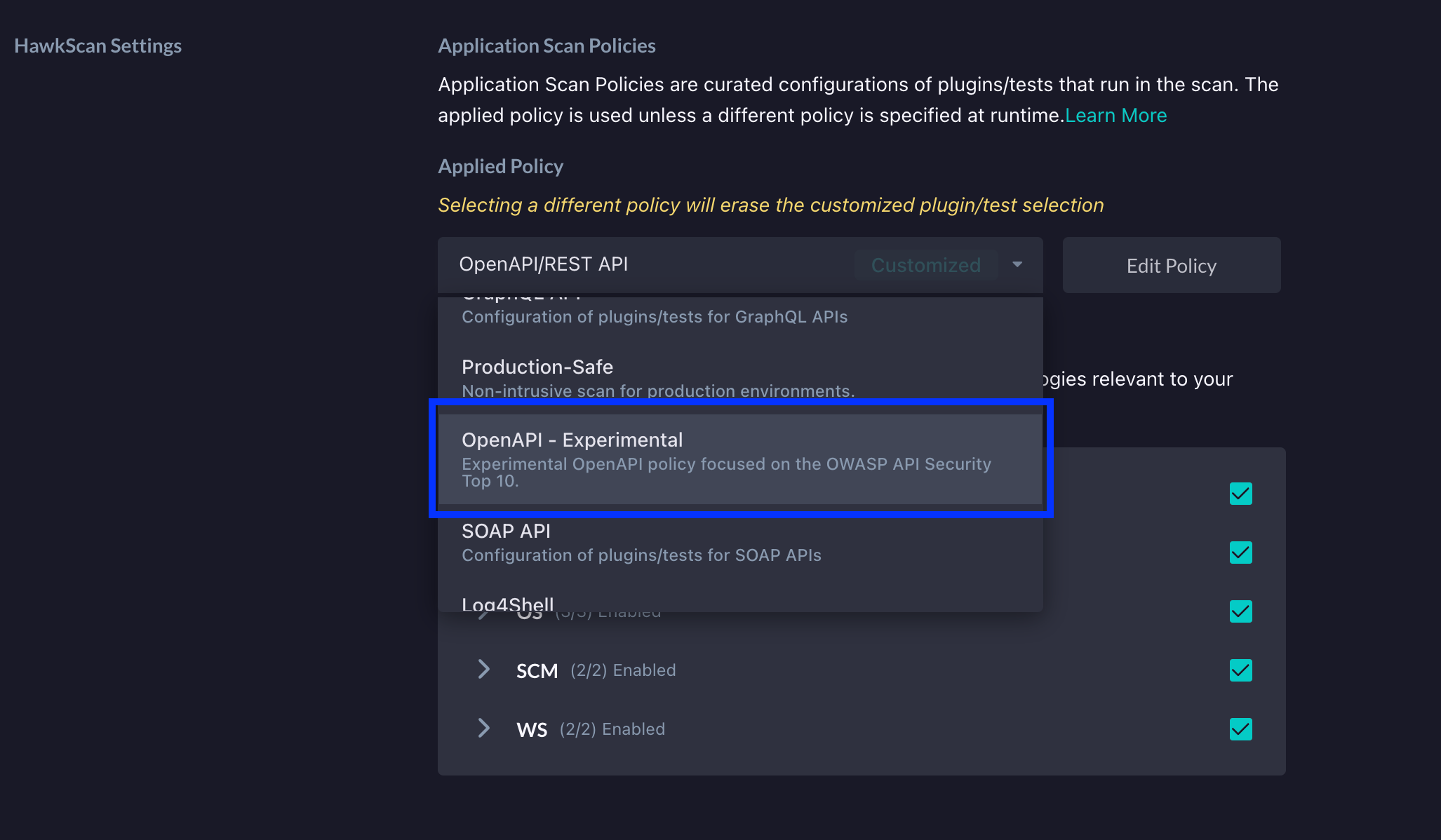
At this point, you can then run HawkScan and begin detecting potential BFLA vulnerabilities. Of course, another way to do this is to simply customize an existing policy to scan for BFLA vulnerabilities. To show how this can be done, we can navigate to the same HawkScan Settings section that we looked at above. From here, we will select the "OpenAPI/REST API" policy from the Applied Policy dropdown.
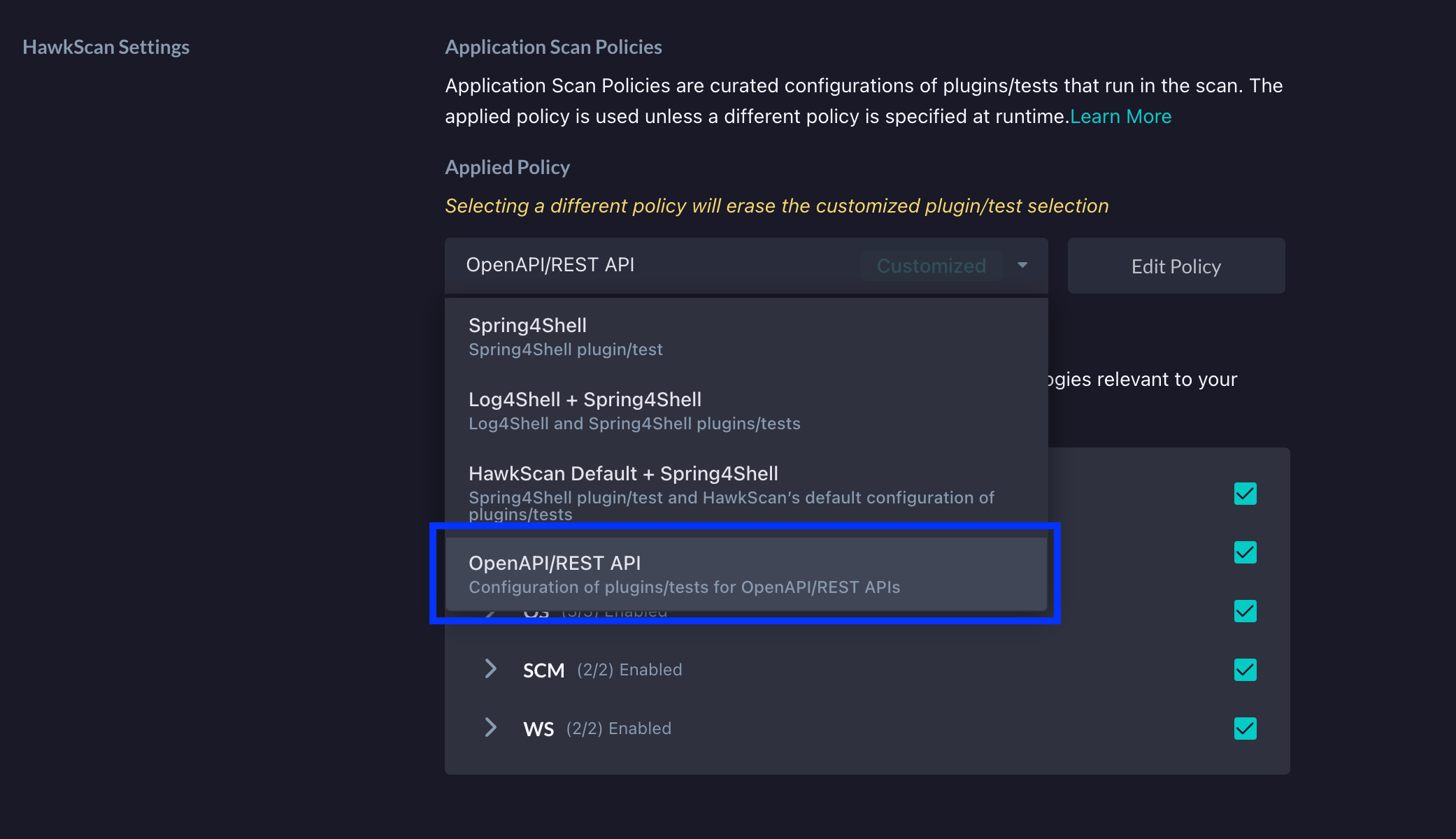
Next, click the Edit Policy button right beside the dropdown.
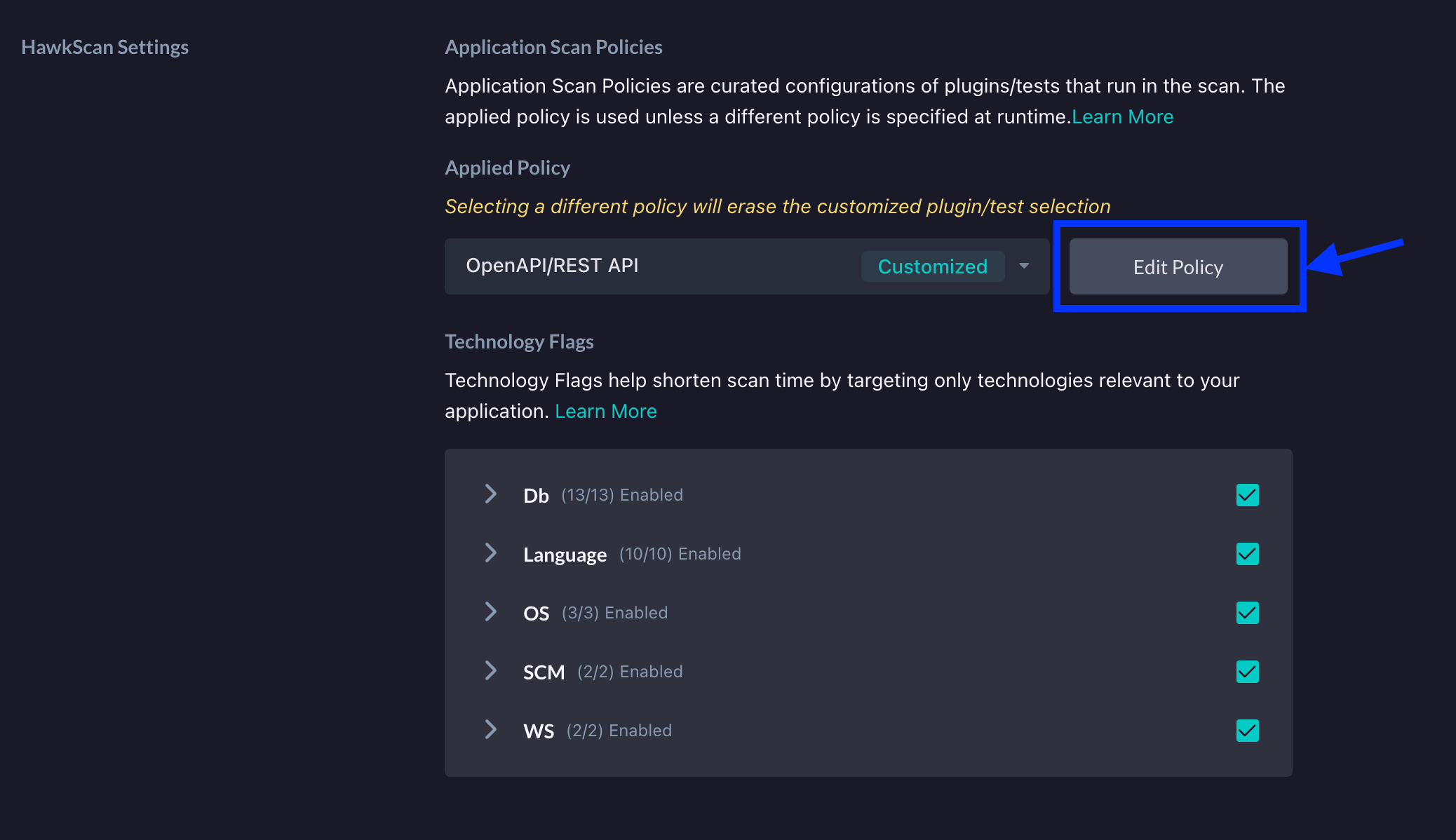
On the next screen, under the Plugins and Tests section, click on the BFLA entry to enable HawkScan to execute tests for potential BFLA vulnerabilities.
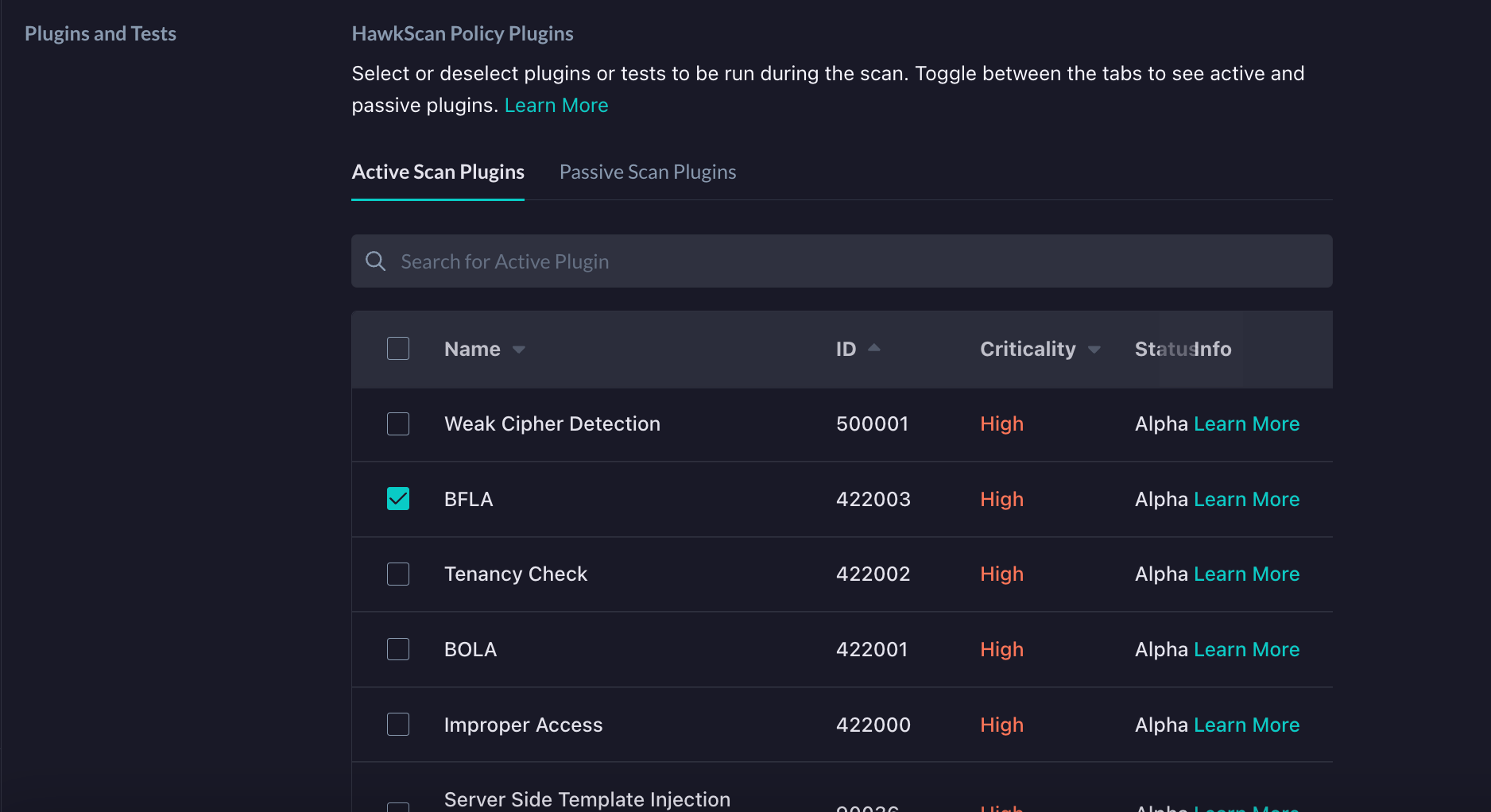
Now, with our application set up in StackHawk, our stackhawk.xml has been added to the root of our API project, and BFLA detection has been enabled, we can finally test our application.
Run HawkScan
To test our application, in a terminal pointing to the root of our project, we will run HawkScan using the following command:
hawk scanAfter running the command, the tests should execute in the terminal.
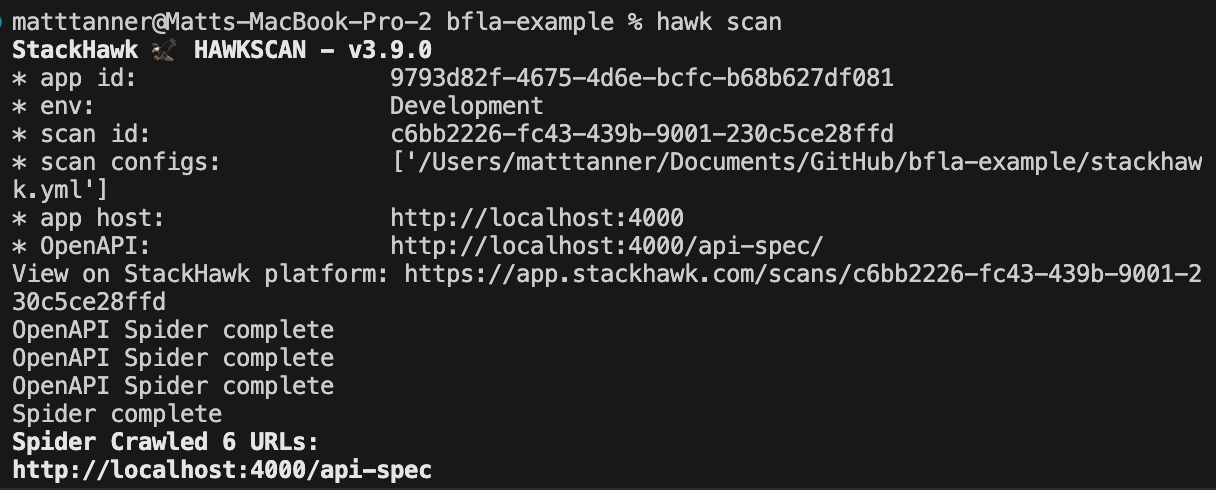
This will run tests against our API based on the OpenAPI spec using the OpenAPI Spider provided by StackHawk.
Explore The Initial Findings
Once the tests are complete, the terminal will contain some information about any vulnerabilities found. Below, we can see that it has identified the BFLA vulnerability that we introduced in the code. To explore this further, we will click on the test link at the bottom of the output. This will take us into the StackHawk platform to explore further.

After clicking on the link, we can now see the test results nicely formatted. Next, we will click the Possible Broken Function-Level Authorization (BFLA) entry.

Within this entry, we can see an Overview and Resources that can help us with fixing this vulnerability as well as the Request and Response that the API returned. Above this, you will also see a Validate button, displaying a cURL command with the exact API request used to expose the vulnerability.

Fixing The BFLA Vulnerability
To fix the BFLA vulnerability in the Flask API, you must implement authentication and authorization checks. This will ensure that users can only access the endpoints that their role permits. In this case, we will look up the database for the user, return their role, and then do the authorization check. This will be done within the `authenticate_and_authorize` function/decorator in the code below.
For simplicity, I'll demonstrate a basic version of these checks. In a real-world application, you can use more robust authentication and authorization mechanisms and platforms like Auth0 or Okta to control access and handle credential creation.
In the code, we will now use PyJWT to check out various aspects of the JWT to authenticate and authorize the user. To install this dependency, run the following in the terminal:pip install PyJWT
Next, to remedy the BFLA vulnerability in the code itself, update your app.py with the following code:
from flask import Flask, jsonify, request
from flask_sqlalchemy import SQLAlchemy
from sqlalchemy.sql import text
from flask_restx import Api, Resource, fields, abort
import jwt
from functools import wraps
JWT_SECRET = 'your_jwt_secret' # Use your JWT secret here
JWT_ALGORITHM = 'HS256' # The algorithm used to sign JWT
def authenticate_and_authorize(f):
@wraps(f)
def decorated(*args, **kwargs):
id = kwargs.get('id')
auth_header = request.headers.get('Authorization')
token = auth_header.split(' ')[1] if auth_header else None
if not token:
abort(401, "Token is missing")
try:
payload = jwt.decode(token, JWT_SECRET, algorithms=[JWT_ALGORITHM])
sub = payload.get('sub')
print(f"User {sub} authenticated")
user = User.query.get(sub)
# Ensure the user information is present and the user is authorized
if user.role != "admin":
abort(403, "Not authorized to access this resource")
except jwt.ExpiredSignatureError:
abort(401, "Token is expired")
except jwt.InvalidTokenError:
abort(403, "Invalid token")
return f(*args, **kwargs)
return decoratedThis code creates a method we will attach to the endpoint. In this code, we will extract the JWT from the Authorization header, then we will read the “sub” claim, which contains the user's ID. We then retrieve the user's role and ensure that their role is “admin” before granting them access to the endpoint. This is a straightforward implementation that will need to be bulked up for production use cases, but it gets the point across. Of course, the JWT Secret is extremely simple since it is just for demonstration purposes. In a production system, you’ll want to have a longer and more complex key that is not directly defined in the code!
We will then add the code below, adding the @authenticate_and_authorize decorator to the PUT route and overwriting the existing route logic that does not require auth.
@ns.doc('update_user', include=False)
@ns.marshal_with(user_model)
@authenticate_and_authorize
def put(self, id):
In this code, we are simply adding one thing to the PUT endpoint in our UserResource class: the @authorize_and_authenticate line, which adds the function we implemented above into the processing of the API request and making sure the user is authenticated and authorized to access the endpoint.
Overall, once these changes are added, the end-to-end code will now look like this:
from flask import Flask, jsonify, request
from flask_sqlalchemy import SQLAlchemy
from sqlalchemy.sql import text
from flask_restx import Api, Resource, fields, abort
import jwt
from functools import wraps
JWT_SECRET = 'your_jwt_secret' # Use your JWT secret here
JWT_ALGORITHM = 'HS256' # The algorithm used to sign JWT
def authenticate_and_authorize(f):
@wraps(f)
def decorated(*args, **kwargs):
id = kwargs.get('id')
auth_header = request.headers.get('Authorization')
token = auth_header.split(' ')[1] if auth_header else None
if not token:
abort(401, "Token is missing")
try:
payload = jwt.decode(token, JWT_SECRET, algorithms=[JWT_ALGORITHM])
sub = payload.get('sub')
print(f"User {sub} authenticated")
user = User.query.get(sub)
# Ensure the user information is present and the user is authorized
if user.role != "admin":
abort(403, "Not authorized to access this resource")
except jwt.ExpiredSignatureError:
abort(401, "Token is expired")
except jwt.InvalidTokenError:
abort(403, "Invalid token")
return f(*args, **kwargs)
return decorated
app = Flask(__name__)
app.config['SQLALCHEMY_DATABASE_URI'] = 'sqlite:////Users/matttanner/Documents/GitHub/bfla-api-example/test.db'
app.config['SQLALCHEMY_TRACK_MODIFICATIONS'] = False
db = SQLAlchemy(app)
api = Api(app, version='1.0', title='User API', description='A simple User API with a BFLA vulnerability')
ns = api.namespace('users', description='User operations')
user_model = api.model('User', {
'id': fields.Integer(readOnly=True, description='The user unique identifier'),
'name': fields.String(required=False, description='The user name'),
'role': fields.String(required=False, description='The user role')
})
class User(db.Model):
__tablename__ = 'users'
id = db.Column(db.Integer, primary_key=True)
name = db.Column(db.String(50))
role = db.Column(db.String(50))
def insert_example_users():
if User.query.count() == 0:
# Only insert if the table is empty to avoid duplicate entries on reload
db.session.add(User(id=1, name="John Doe", role="admin"))
db.session.add(User(id=2, name="Jane Smith", role="user"))
db.session.add(User(id=3, name="Alice Johnson", role="user"))
db.session.commit()
@ns.route('/<int:id>', methods=['GET', 'PUT'])
@ns.response(404, 'User not found')
@ns.param('id', 'The user identifier')
class UserResource(Resource):
@ns.doc('get_user')
@ns.marshal_with(user_model)
def get(self, id):
"""Fetch a user given its identifier"""
try:
# Use parameterized SQL query to prevent SQL injection
query = text("SELECT * FROM users WHERE id = :id")
# Execute the query with safe parameter substitution
result = db.session.execute(query, {'id': id})
user = result.fetchone()
if user:
return user
else:
api.abort(404)
except Exception as e:
# Handle the exception here
print(f"An error occurred: {str(e)}")
api.abort(500, f"An error occurred: {str(e)}")
@ns.doc('update_user', include=False)
@ns.marshal_with(user_model)
@authenticate_and_authorize
def put(self, id):
"""Update a user given its identifier"""
try:
# Use parameterized SQL query to prevent SQL injection
query = text("UPDATE users SET name = :name, role = :role WHERE id = :id")
data = request.get_json(silent=True)
# Check if request body exists
if data:
# Execute the query with safe parameter substitution
db.session.execute(query, {'id': id, 'name': data['name'], 'role': data['role']})
db.session.commit()
return User.query.get(id)
except Exception as e:
# Handle the exception here
print(f"An error occurred: {str(e)}")
api.abort(500, f"An error occurred: {str(e)}")
# Serve the OpenAPI spec at /api-spec/
@app.route('/api-spec/')
def api_spec():
# Manually remove the PUT endpoint documentation
if '/users/{id}' in api.__schema__['paths']:
if 'put' in api.__schema__['paths']['/users/{id}']:
del api.__schema__['paths']['/users/{id}']['put']
# Set the server URL
api.__schema__['basePath'] = 'http://localhost:4000'
return jsonify(api.__schema__)
if __name__ == '__main__':
with app.app_context():
db.create_all()
insert_example_users()
app.run(debug=True, port=4000)
Once the code has been updated on your side, you can stop the currently running server (by using ctrl + C in the terminal) and restart it with the new code using:
flask run –port=4000The app should now be up and running with the updated code!
Confirm the fix!
With the latest code, users must send a JWT along with their request in the Authorization header. The code will then extract the sub field, retrieve the user's role from the database, and then check to ensure they have the admin access needed to perform the function they are trying to do. In the JWT.io debugger, this is how such a token would look:
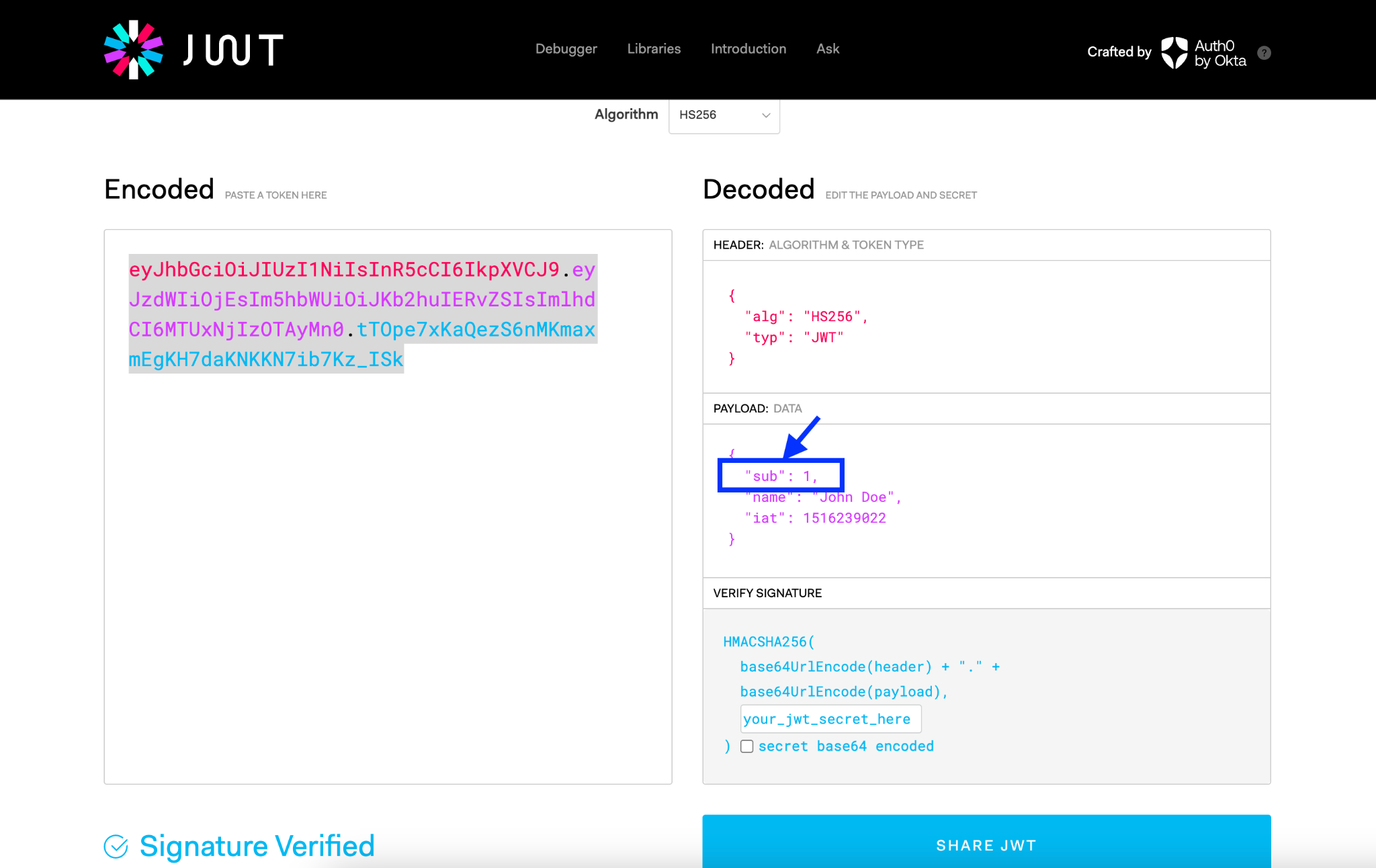
Now, let’s confirm the fix in StackHawk. We will click the Rescan Findings button back in StackHawk to do this.

Then, we will see a modal containing the “hawk rescan” command that includes the correct Scan ID. You’ll run this command in the same terminal where you ran the initial set of tests.
In the output, you will again see any vulnerabilities in the scan. In this case, you’ll see that the BFLA vulnerability is no longer showing. Clicking on the link at the bottom of the terminal output, you can confirm that the BFLA vulnerability has now been added to the Fixed Findings from Previous Scan, confirming that the vulnerability has been successfully fixed and has passed any vulnerability tests.

With that, we’ve successfully remedied and retested our API to ensure its safety from potential BFLA attacks. Please remember that the code above is for demonstration purposes and that adding robust, production-grade authorization to an API endpoint is much more involved than we implemented above. Using an API gateway, Role-based Access Control (RBAC), and identity provider, such as Auth0, is one of the best ways to prevent BFLA and secure your APIs from unauthorized use.
Why StackHawk?
When it comes to preventing vulnerabilities, such as BFLA, StackHawk offers a comprehensive platform for developers to secure their applications and APIs. StackHawk is a modern, powerful DAST tool designed for developers to integrate application security testing seamlessly into their software development lifecycle. It is not just another security tool; it's a developer-first platform emphasizing automation, ease of use, and integration into existing development workflows.
At its core, StackHawk is built around empowering developers to take the lead in application security. It provides a suite of tools that make it easy to find, understand, and fix security vulnerabilities before they make it to production. One of the critical components of StackHawk is HawkScan, a dynamic application security testing (DAST) tool that scans running applications and APIs to identify security vulnerabilities.
With StackHawk, developers and security teams can:
Automate Security Testing: Integrate security testing into CI/CD pipelines, ensuring every build is automatically scanned for vulnerabilities.
Identify and Fix Vulnerabilities: Receive detailed, actionable information about each vulnerability, including where it is in the code and how to fix it.
Test in All Environments: Use StackHawk in various environments, including development, staging, and production, to catch security issues at any stage of the development process.
Customize Scans: Tailor scanning configurations to suit specific applications and environments, ensuring more relevant and accurate results.
By focusing on a developer-first approach to security testing and integrating smoothly into existing dev tools and practices, StackHawk demystifies application security, making it a more approachable and manageable part of the software development lifecycle.
Conclusion
In this blog, we have looked deeply into the complexities of Broken Function Level Authorization (BFLA) vulnerabilities. We unpacked the essence of BFLA, revealing how it emerges from insufficient authorization checks, allowing attackers to access functions beyond their permissions. The discussion illuminated the root causes, mainly seen through the lack of validation and authorization in API requests. We looked into understanding BFLA's mechanics and the significance of adopting a defense strategy encompassing strong authorization checks, RBAC, and a zero-trust approach, among other security best practices.
From a practical perspective, we looked at how to identify a BFLA vulnerability within a Flask application using StackHawk, a cutting-edge Dynamic Application Security Testing (DAST) tool designed for developers. By integrating security testing directly into the development workflow, StackHawk pinpointed the BFLA vulnerability and provided actionable insights to remediate it effectively. Through a simple example, we showcased the power of adding authentication and authorization middleware to secure API endpoints against unauthorized access, thus mitigating the BFLA threat we introduced in the original code.
Embracing StackHawk in your development cycle equips your team with the necessary tools and insights to tackle security vulnerabilities, including BFLA, preemptively. This approach not only enhances the security posture of your applications but also fosters a culture of security mindfulness among developers. Experience firsthand how StackHawk's seamless integration and developer-centric solutions can transform your application security testing workflow, ensuring your applications are robust against common API threats outlined in the OWASP API Security Top 10. Sign up for a free trial of StackHawk today and join the ranks of proactive developers who are “shifting left” and making API security an integral part of their development process with StackHawk.



