In a time where API security is paramount, the adoption of gRPC (gRPC Remote Procedure Calls) is on the rise, offering advantages like performance gains and language-agnostic interfaces. However, the security aspects of gRPC remain a challenge and a mystery.
In this blog post, StackHawk engineers Dana White and Austin Pearigen break down the challenges of securing gRPC services and provide solutions through the lens of Dynamic Application Security Testing (DAST).
What is DAST?
Dynamic Application Security Testing (DAST) is a technique that mimics a hacker's actions to identify vulnerabilities in a live application. It explores the full surface of your application, checking for issues like SQL injection, among others. At StackHawk, we've developed a tool that enables this kind of testing, allowing engineers to shift security left in the development process.
Challenges in gRPC Security
Authentication
Authentication is always a challenge, especially when it's designed not to be automated. Legacy systems often have complex authentication mechanisms that are poorly documented. To address this, we've built a developer tool, Hawk Perch, that uses gRPC to iterate quickly on authentication configurations. This tool provides real-time feedback, making it easier to test and adjust authentication mechanisms. See how it works below.
Scanning gRPC Services
Traditionally, DAST tools have been limited to HTTP/1-based services. However, gRPC runs over HTTP/2, which presents a challenge for traditional scanners. We've extended our tool to support gRPC, allowing us to test these services directly.
How We Scan gRPC Services
File Descriptor Set
To understand a gRPC service, we use a file descriptor set, which can be generated from the service itself or accessed via reflection. This descriptor set provides us with the information we need to understand the service's schema.
Dynamic Messages
We use gRPC's Dynamic Message class to construct messages at runtime. This allows us to generate messages based on the file descriptor set, which we can then send to the gRPC service for testing.
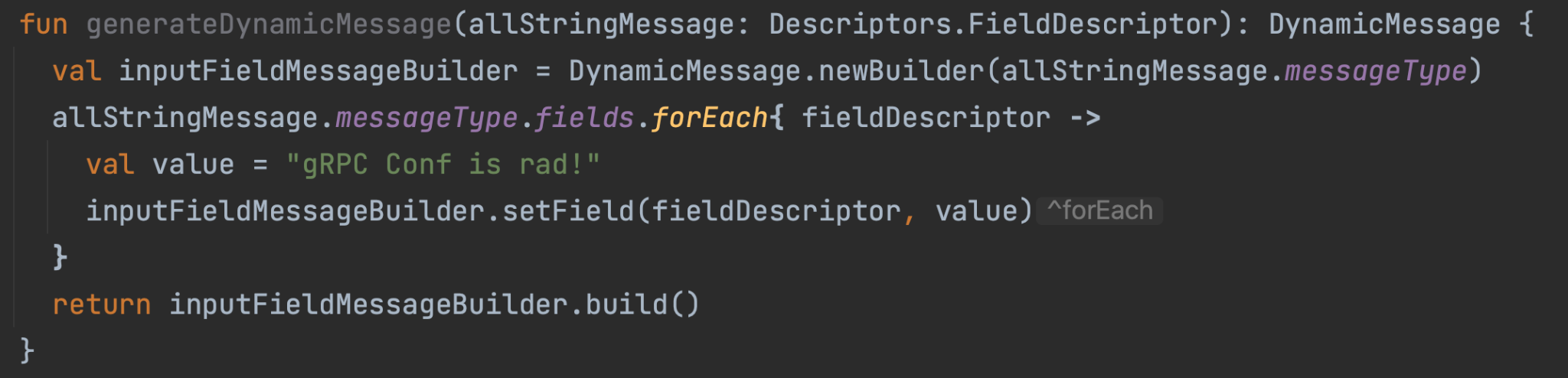
Custom Variable Injection
Our tool supports custom variable injection, allowing you to specify particular values for certain fields. This is useful for testing different logic branches in your code. Below is an example configuration using custom values:
# in the "app" config...
app:
grpcConf:
filePath: '/resources/main/descriptor_set.pb'
customVariables:
# List of custom variables and a list of possible values to use for each of them.
customVariables:
- field: firstName
values:
- customFirstName1
- customFirstName2
- field: lastName
values:
- customLastName1
- customLastName2
- field: username
values:
- customUsername1
- customUsername2
- customUsername3Scanning gRPC Services with StackHawk
In this video, we demonstrate how the StackHawk platform works, showing a scan against a vulnerable gRPC application. The scan identifies various vulnerabilities, including SQL injection. Our platform provides detailed information on each vulnerability, along with remediation steps.
FAQs
Does StackHawk scan for vulnerabilities other than SQL injection?
Yes, our tool checks for a wide range of vulnerabilities, including all the OWASP Top 10.Is an agent required?
No, as long as we can access the application, we can scan it. We recommend running the scanner as close to the application as possible for latency reasons.Is it free to get started?
Yes, we offer a free trial account where you can scan a single application as much as you want.

Wrapping it up!
Security is a critical aspect of any application, and gRPC services are no exception. With the right tools and practices, you can identify and fix vulnerabilities before they become a problem. At StackHawk, we're committed to making this process as seamless as possible, helping you secure your applications effectively.
Dana White and Austin Pearigen are Software Engineers at StackHawk
Get started today:



