When HawkScan scans an application, it uses a scan policy to determine which vulnerability tests to run against that app. Scan policies are a collection of enabled and disabled plugins, and plugins can be thought of as individual vulnerability tests. The plugins that are enabled in the scan policy will be run when HawkScan uses that scan policy to scan an application.
With default settings, HawkScan will run its default scan policy with a curated selection of plugins based on their quality and general applicability for use with any application. We also provide scan policies for other use cases, such as scanning against OpenAPI/REST, GraphQL, or SOAP applications, or scanning for the Log4Shell vulnerability. Traditionally, this has been configured from the StackHawk YAML configuration file.
Now scan policy settings can be managed directly for each application within the StackHawk Platform. Not only can scan policies be selected for use with HawkScan, but now they can be customized by allowing fine-tuned control over which plugins are enabled and disabled within the scan policy.
Visual learner? Jump to the video overview
Selecting a Scan Policy
Scan policies can be set for an application on the settings page for that application. For example, if we are scanning an application with a REST API, we can select the OpenAPI/REST API scan policy, which will run a selection of enabled plugins customized for REST applications. Within the application's settings, we can change the policy from "HawkScan Default" to "OpenAPI/REST API."
Now subsequent scans against this application will use the OpenAPI/REST API scan policy. For best results, it is suggested to specify an OpenAPI spec in your StackHawk YAML configuration when running this application scan policy. More on that here.
Customizing a Scan Policy
To customize a scan policy, we can select any of the available scan policies and click the "Customize Policy" button. As an example, I will use the "HawkScan Default" scan policy for a scan against a vulnerable Django app.
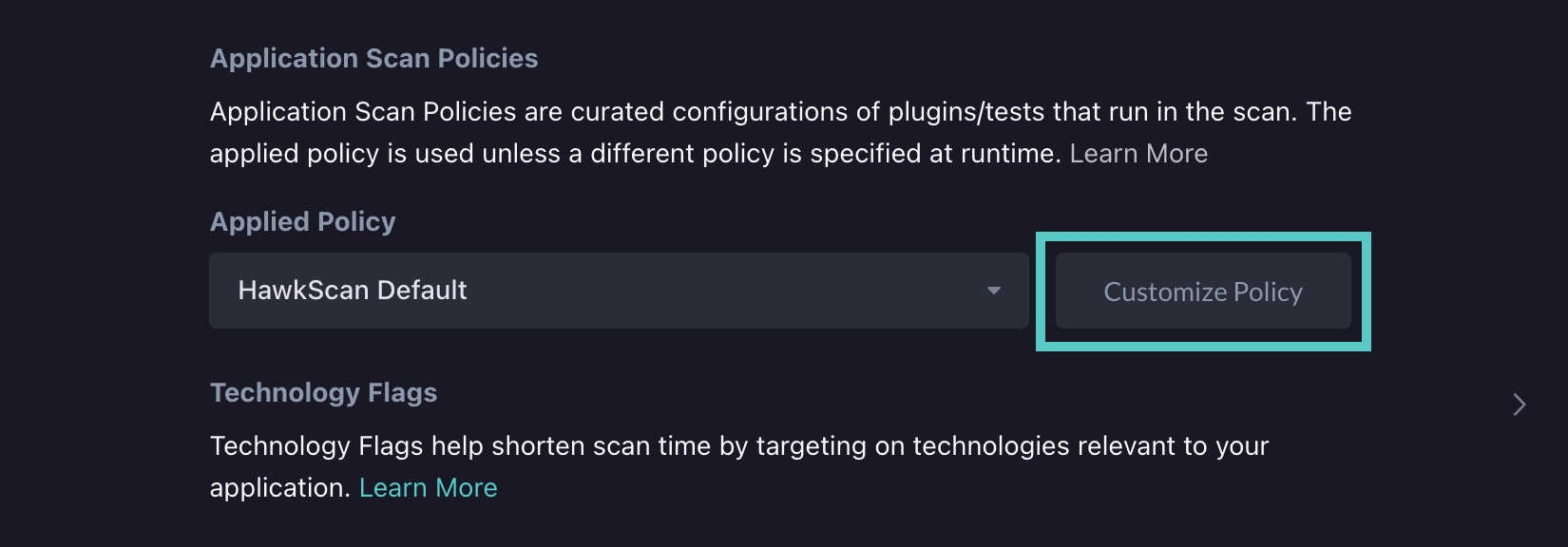
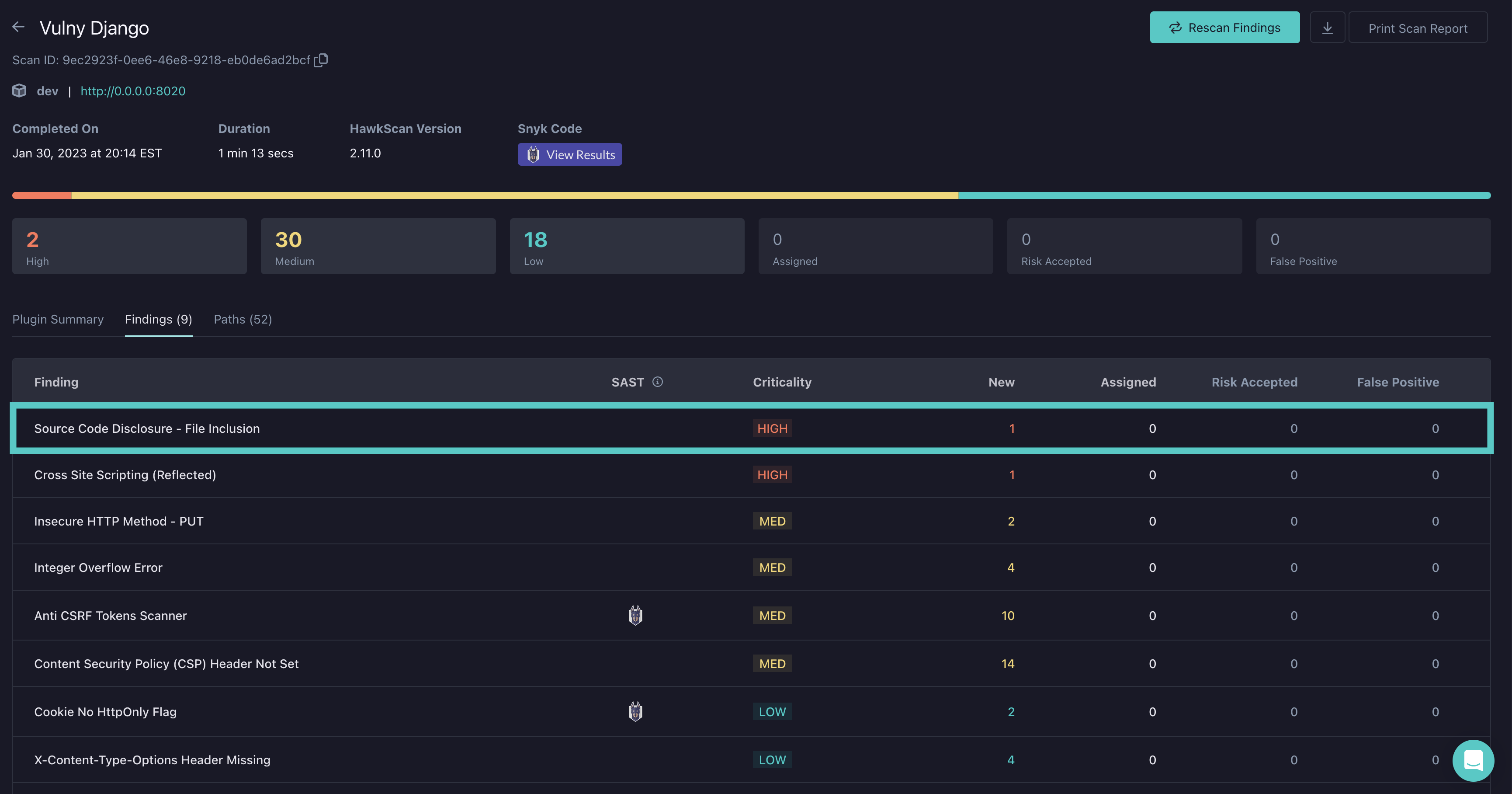
This will bring us to a page that shows us all available active and passive plugins that can be run with HawkScan. Checking or unchecking one of the plugins will enable or disable that plugin. When customizing a policy, there will already be some plugins that are enabled. In this example, I will enable a plugin that is disabled by default in the HawkScan default scan policy called "Source Code Disclosure - File Inclusion" (ID 43). This test detects vulnerability to directory traversal attacks. I will also disable a plugin called "Proxy Disclosure" (ID 40025) due to that plugin sometimes experiencing false positives.
First I find these plugins in the active plugins list and check/uncheck them.
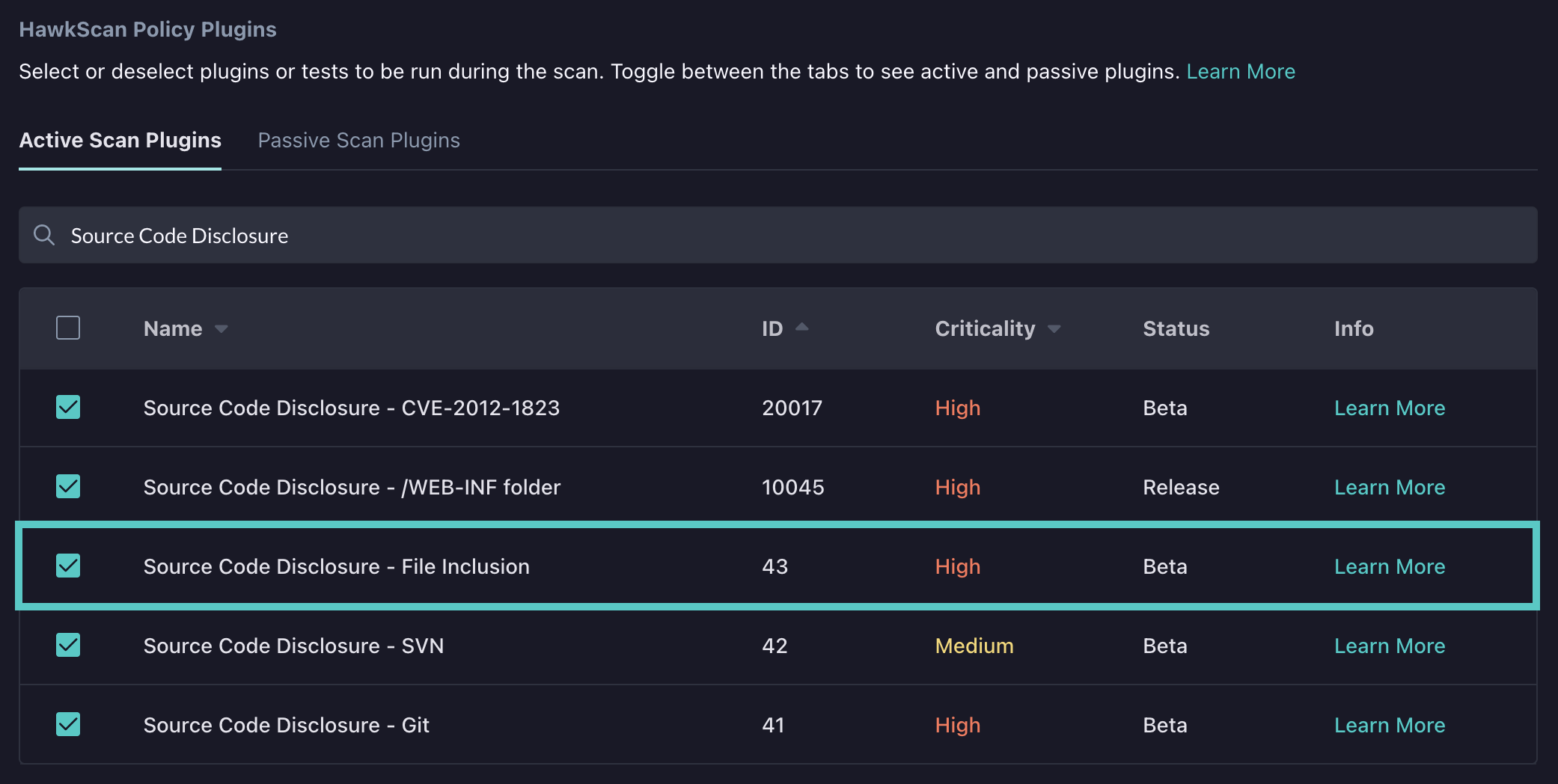
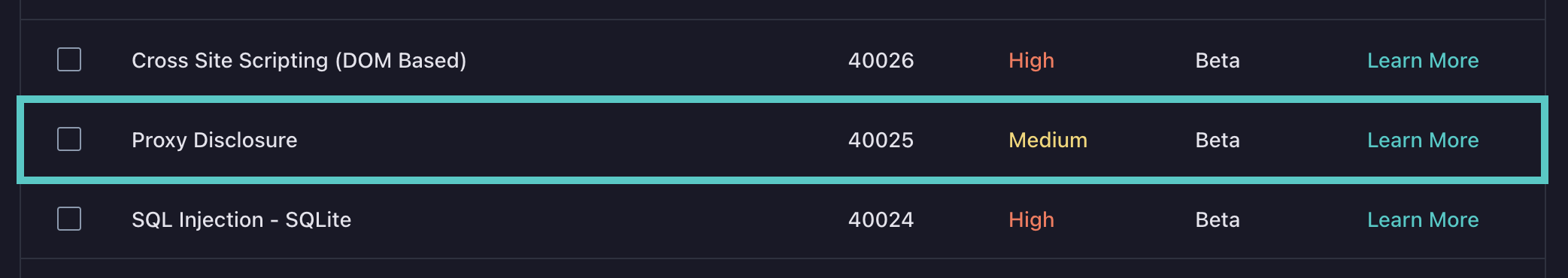
Toggling these check boxes will save the application scan policy. By backing out to the application settings page, the application scan policy will now be labeled as customized.
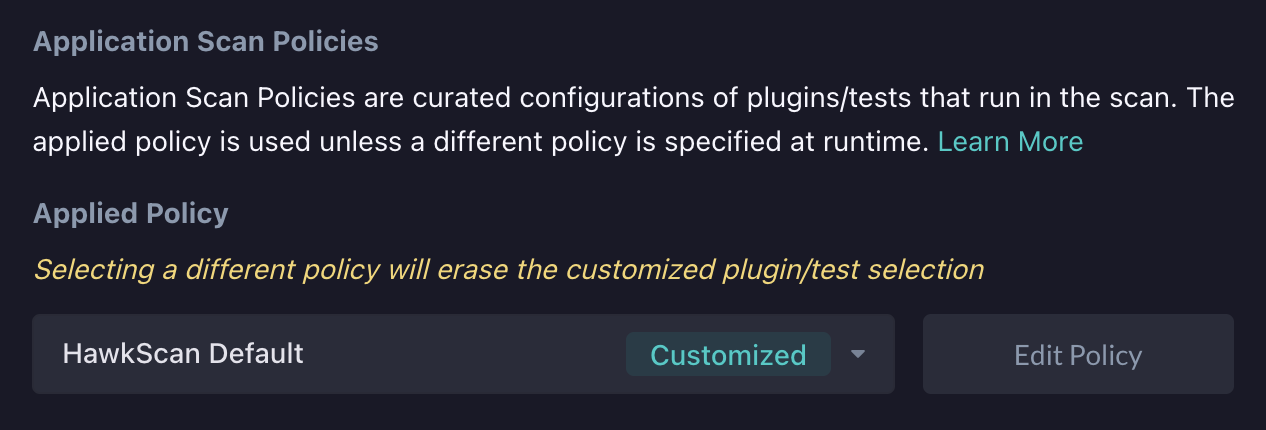
Now it's time to run a scan. If we run a scan against this application, it will use the customized scan policy. Below you can see that the plugin added to the scan policy fired an alert as the corresponding vulnerability was discovered in the app.
I hope you enjoyed reading about our new Scan Policy Management feature. If you'd like to learn more, check out our docs on this feature.



