StackHawk and GitHub work together to help developers find and fix security vulnerabilities in their normal workflows and give security teams full visibility into their entire attack surface. The integration combines the power of StackHawk's dynamic application and API security testing capabilities with GitHub's collaborative platform to introduce a modern developer-first approach to security testing.
But what does developer-first security mean?
An application security tool being "developer-first" means that it prioritizes the needs and workflows of developers when it comes to identifying and fixing security issues in software applications. Here are the criteria for a developer-first security tool:
Easy to integrate: A developer-first security tool can seamlessly integrate into the developer's existing workflow and tools, such as CI/CD pipelines and source code managers. It levels up their coding processes without disrupting them.
User-friendly: The tool has to have an intuitive user interface and provide clear, actionable insights into security vulnerabilities. Developers don't want to waste time deciphering complex reports and going down rabbit holes; they want straightforward guidance on how to fix the issue.
Low false positives: Nothing frustrates developers more than dealing with a flood of false positives. A developer-first tool minimizes false alarms, ensuring that developers can easily prioritize and focus on real issues.
Automation: The tool must automate security testing as much as possible and catch vulnerabilities early in the development cycle. Developers run automated unit and integration tests and fix code as they are working on it, not months later once it’s in production.
Customization: Developers have different needs, preferences, and techstacks. A developer-first tool allows customization, so developers can tailor security testing to their specific requirements.
Developer-first security testing with StackHawk and GitHub
StackHawk offers a number of powerful integrations within the GitHub ecosystem, enhancing the developer experience and making security testing seamless. Let's take a closer look at four key integrations:
GitHub Insights
GitHub Insights provides continuous discovery and visibility of your organization's entire attack surface from the inside out.
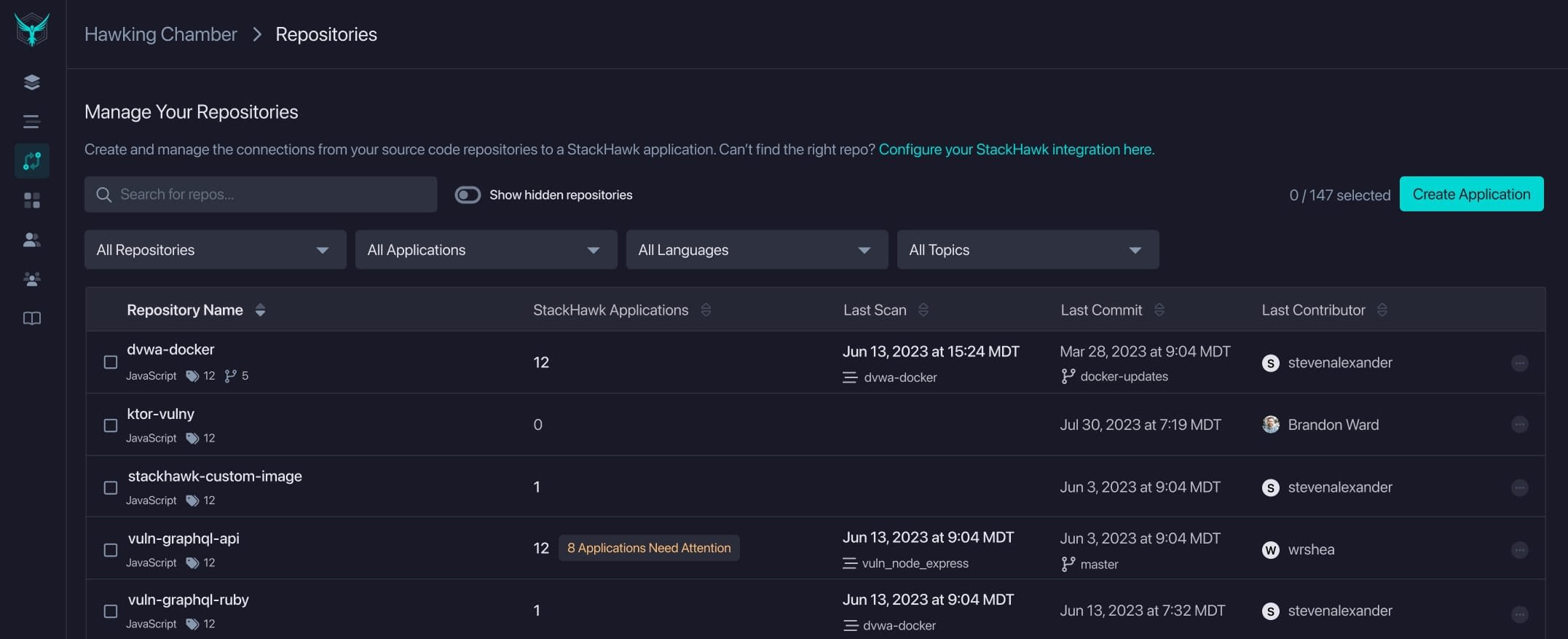
For security teams, the Repositories page is a goldmine of information. It enables them to continuously monitor and assess the security of API and application assets across the organization. This level of visibility ensures that security measures can be put in place for new assets as they are added, and existing measures can be adjusted as needed— a crucial capability with how quickly new routes and endpoints are deployed today.
How it works
StackHawk pulls metadata from your organization's repositories into the StackHawk platform for security teams to easily track and monitor coverage on a single page.
You can view details such as repo name, the StackHawk Application it’s mapped to, last commit and scan date, and last contributor to help understand the full scope of your organization's attack surface and collaborate with developers more efficiently.
Learn more about GitHub Insights
GitHub Actions
GitHub Actions enables automated security testing in your continuous integration/continuous deployment (CI/CD) pipeline. This feature brings security testing up to speed with software development as it allows you to automatically test your code for security issues at the same time as your regular testing processes like unit and integration testing.
This means every time a developer checks in code, you can automatically test your application and discover any new security issues as soon as they are introduced and fix them before they ever reach production.
How it works
The HawkScan action found in the GitHub Actions Marketplace simplifies embedding StackHawk into GitHub Actions workflows. It’s a comprehensive action that is easy to configure and has the flexibility to handle complex use cases.
The HawkScan Action can run most tests with just a single parameter, your StackHawk API key, and a four-step workflow. For example, to scan a Node.js app, your GitHub Actions workflow would be as simple as this:
# .github/workflows/hawkscan.yml
name: HawkScan
on:
push:
jobs:
hawkscan:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v2
- run: npm install
- run: nohup node bin/www &
- uses: stackhawk/hawkscan-action@v1.1
with:
apiKey: ${{ secrets.HAWK_API_KEY }}Learn more about the HawkScan Action
Pull Request Checks
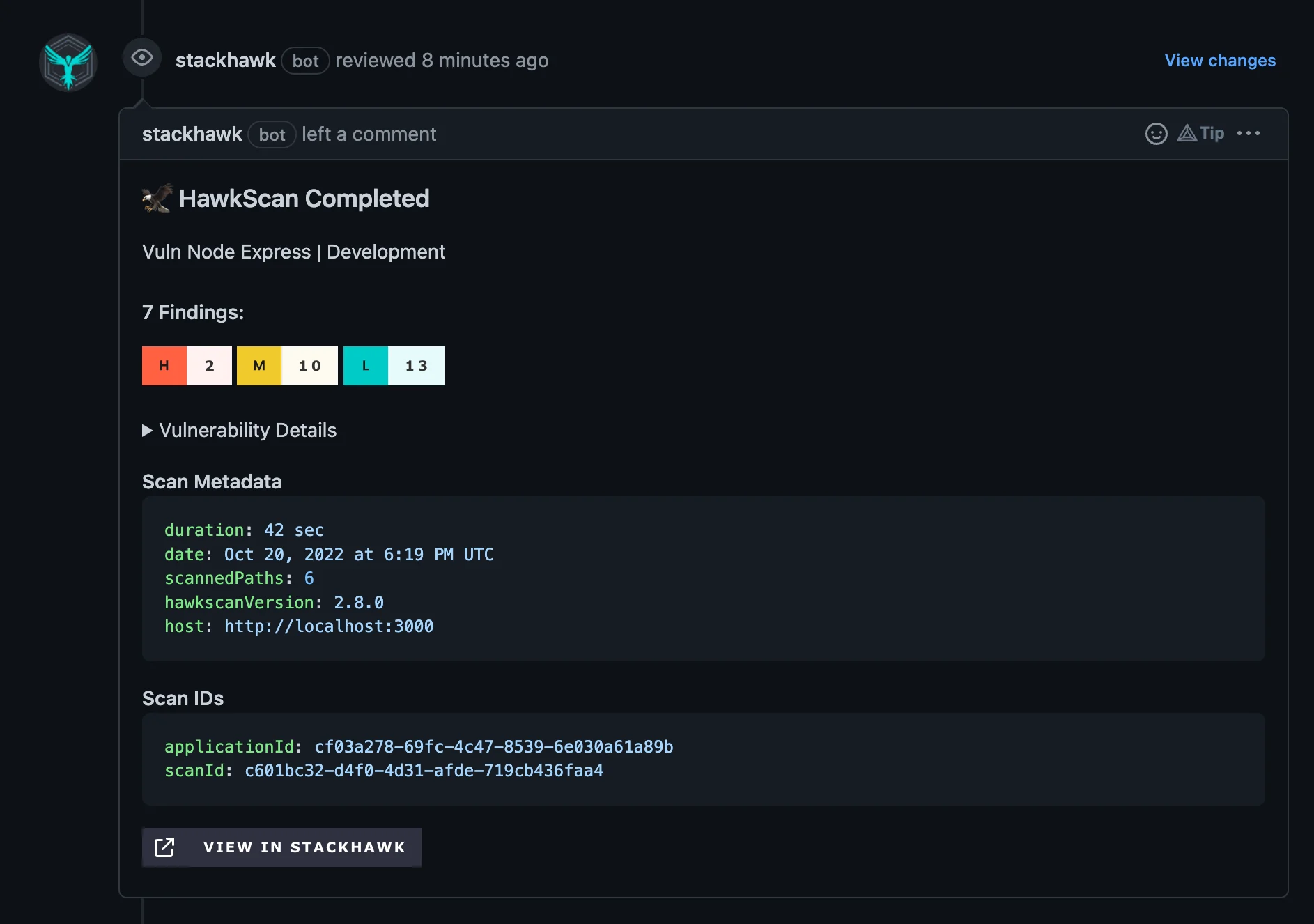
GitHub Pull Request Checks deliver security feedback to developers on every pull request. By automating testing in a CI/CD pipeline, we are able to provide a few configuration options that allow your pipeline to explain how each scan maps back to your source code’s history. This creates a fast feedback loop for developers by associating scan results with the specific pull request, branch, and commit information. StackHawk then leverages this context to post test results as comments on the pull request.
The ultimate goal is to help developers iterate faster and be confident they are upholding the security requirements of the application.
How it works
When someone submits a pull request, and before it's merged into the main codebase, StackHawk's integration with GitHub automatically checks it for security vulnerabilities. If any issues are identified, rich test details are commented right in the pull request, alongside regular code reviews. This immediate feedback loop allows developers to address security concerns as they come up, rather than dealing with them later in the development cycle. It's a win-win for both developers and security teams, fostering collaboration and proactive security practices.
Learn more about Pull Request Checks
CodeQL
The GitHub CodeQL integration takes operational efficiency to the next level. It correlates dynamic application security testing (DAST) and static application security testing (SAST) vulnerability findings to provide developers with precise information about where an exploitable vulnerability lives in their codebase.
This level of granularity is a game-changer for developers, as it enables them to fix security issues faster and with greater precision. They don’t have to sift through endless lines of code trying to identify the root cause of a vulnerability; they can jump right into recreating and fixing the issue instead.

How it works
Once a StackHawk Application is mapped to a GitHub repository, scan results in StackHawk will display a GitHub badge when findings from both tools are matched based on the CWE ID.
If StackHawk finds an exploitable vulnerability and GitHub identifies that same issue, the vulnerability request and response information from StackHawk is reconciled with the exact line of code causing the issue from GitHub.
Give it a try!
StackHawk's deep integrations with GitHub change the way developers interact with security. By embedding security testing seamlessly into their workflows, developers can proactively fix vulnerabilities in the context of their code, significantly reducing the risk of introducing bugs into production and the time it takes to fix them. With GitHub Insights, the HawkScan Action, Pull Request Checks, and CodeQL Integrations, StackHawk empowers developers to build secure code efficiently and effectively.
Sign up for a free trial of StackHawk and look for the HawkScan Action in the GitHub Actions Marketplace or the StackHawk app in the GitHub Applications Marketplace to get started today.



