As Application Programming Interfaces (APIs) have grown in use and abundance, so has the number of attacks and breaches stemming from said APIs. The OWASP API Security Project and OWASP API Security Top 10 have helped to highlight the types of vulnerabilities that developers should be conscious of and defend against.
APIs are not only the backbone of modern application architecture, but they are also vital for maintaining security. Typically, a company’s most valuable and sensitive data resides behind an API. Delivering secure applications relies on ensuring that the underlying APIs are free from security vulnerabilities.
Delivering secure APIs, however, is easier said than done. APIs sit at the intersection of engineering and security teams, and typically see rapid iteration as software is built and improved. Ensuring API security raises questions such as:
Which team is responsible for maintaining API security?
How do we ensure that updates to our APIs do not create a vulnerability?
Does our team have API security testing?
Modern software development teams are solving this problem with developer-centric API security testing automated in CI/CD. The rest of this post has more information on what API security testing is, how it works, and what to look for in selecting a top security testing vendor. Read on to learn more.
What is API Security Testing?
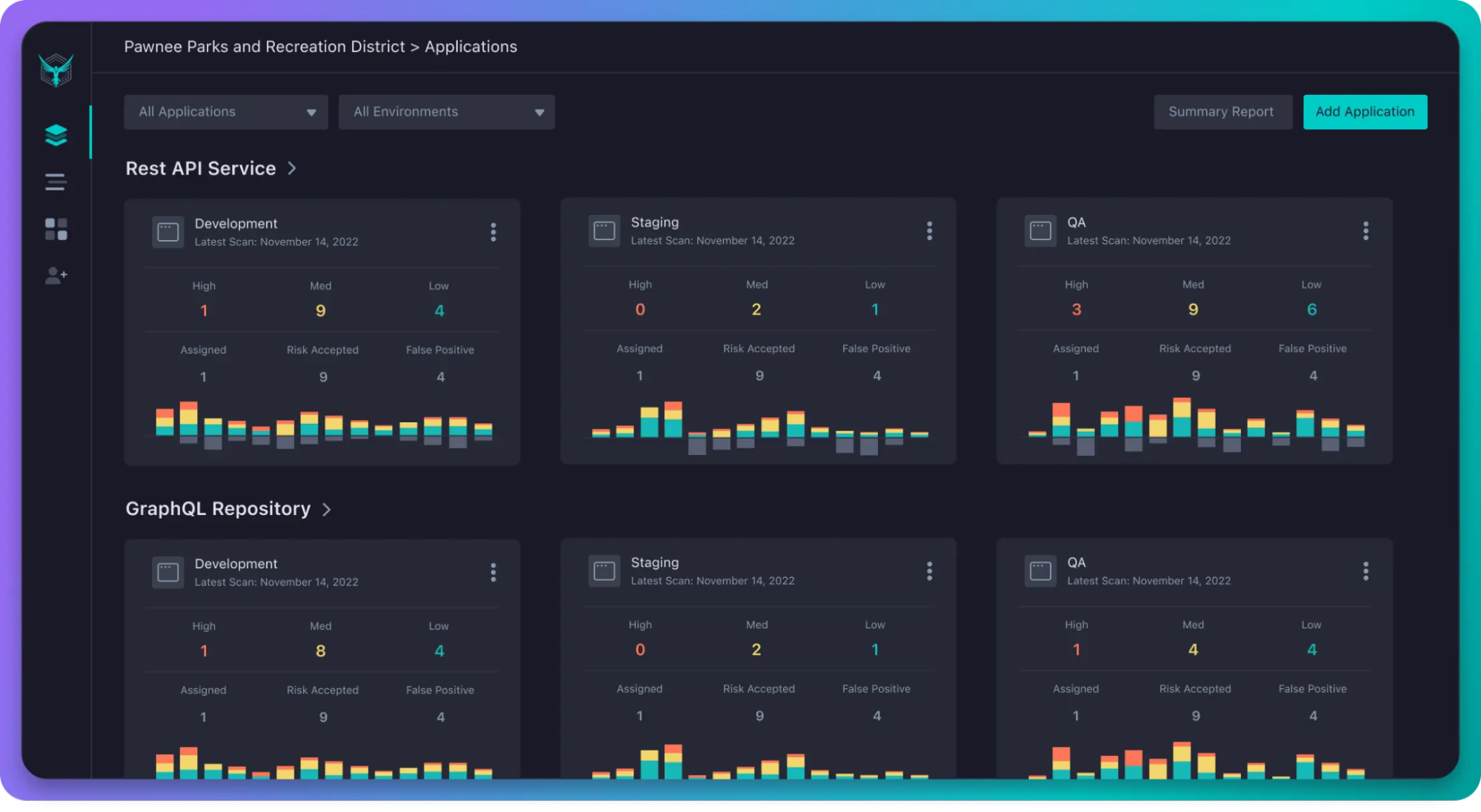
API security testing is the process of identifying vulnerabilities in APIs to ensure that they are secure against potential threats. APIs serve as the backbone of modern applications, connecting different systems and allowing data exchange, which make them a prime target for attackers. By performing security tests, teams can discover vulnerabilities such as improper authentication, data exposure, or other business logic vulnerabilities, flaws that could be exploited by malicious actors. Ensuring the security of APIs is vital to protect both the underlying infrastructure and sensitive data.
The Adoption of DevOps Practices
Historically, API security testing was conducted by enterprise security teams through manual scans and penetration testing. These methods were often time-consuming and occurred late in the development cycle, leading to the delayed discovery of issues.
However, with the adoption of DevOps practices, API security testing is increasingly integrated into the software development lifecycle (SDLC). This shift to continuous testing as part of the DevOps pipeline allows developers to catch security issues early, reduce vulnerabilities, and respond more quickly to potential threats, thereby improving the overall security posture of their applications.
Understanding API Security Risks
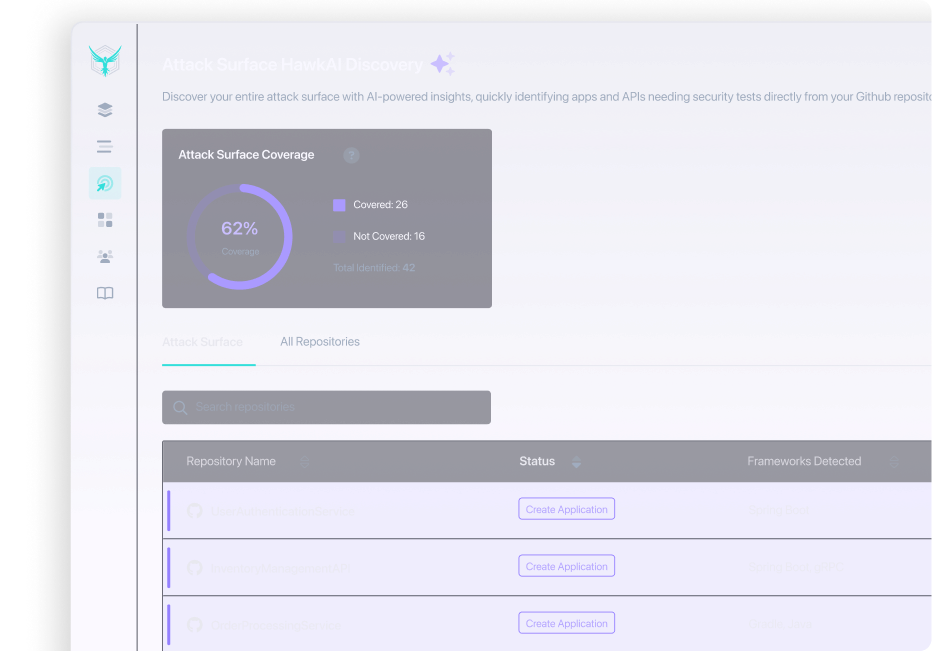
APIs are critical to modern applications, but they are also vulnerable to various security risks. Understanding these risks is key to developing an effective API security strategy and safeguarding data, systems, and operations. Below, we explore some of the most common API security threats.
Injection Attacks
Injection attacks, such as SQL or command injections, occur when untrusted data is sent to an interpreter, resulting in unintended commands being executed. APIs are particularly vulnerable to this type of attack when they do not properly validate and sanitize inputs. An attacker can use this weakness to manipulate queries or execute commands, leading to data theft, corruption, or control over the system. To reduce the risk of injection attacks, it is essential to implement input validation and use parameterized queries.
Broken Authentication and Session Management
APIs often handle authentication and session management, which are common targets for attackers. Weaknesses in these areas can result in unauthorized access to sensitive information or the hijacking of user sessions. Broken authentication occurs when API keys, tokens, or credentials are improperly managed or exposed, allowing attackers to impersonate users. Implementing strong authentication methods, such as OAuth or multi-factor authentication (MFA), can help minimize this risk.
Insecure Direct Object References (IDOR)
Insecure direct object references occur when an API exposes internal objects, such as files or database records, to unauthorized users. This vulnerability enables attackers to tamper with input, allowing them to access data they shouldn't be able to. For instance, an attacker could alter an API endpoint to gain unauthorized access to another user's information. To mitigate the risk of IDOR, it is vital to enforce strict access controls and thorough authorization checks.
Denial-of-Service (DoS) Attacks
Denial-of-service (DoS) attacks are designed to overwhelm an API with excessive requests, rendering it unavailable to legitimate users. Attackers can exploit weaknesses in the API’s rate limiting or request handling mechanisms, leading to service outages. Implementing rate limiting, throttling, and monitoring can help mitigate the risk of DoS attacks and ensure that APIs remain operational under stress.
Consequences of API Security Risks
The consequences of failing to address API security risks can be severe, including data breaches, reputational damage, and financial losses. A successful attack can lead to the exposure of sensitive customer or business data, resulting in a loss of trust and potential legal penalties. In more extreme cases, compromised APIs can give attackers control over critical systems, amplifying the scope of damage.
By understanding these risks and adopting proactive security measures, organizations can significantly reduce their exposure to API-related threats and maintain the security of their applications and data.
Preparing for API Security Testing
Effective API security testing begins with thorough preparation, which includes setting up a reliable testing environment, identifying the scope of testing, and ensuring the right tools and resources are in place.
Setting Up a Testing Environment
Creating a testing environment that mirrors the production environment as closely as possible is critical for obtaining accurate results. This means replicating the same API configurations, authentication mechanisms, and traffic conditions that exist in the live environment. By doing so, you can identify vulnerabilities that may only surface under real-world conditions. The testing environment should also be isolated to prevent any unintended impacts on production data or systems.
Defining the Scope of Testing
Before starting, it's essential to define the scope of the security testing to ensure that all critical aspects of the API are examined. This involves identifying which endpoints, authentication mechanisms, data flows, and external integrations need testing. Scoping should also consider the types of threats you're most concerned about, such as injection attacks, data exposure, or unauthorized access, to tailor the testing approach accordingly. A well-defined scope helps focus security testing efforts and ensures comprehensive coverage of potential vulnerabilities.
Gathering Tools and Resources
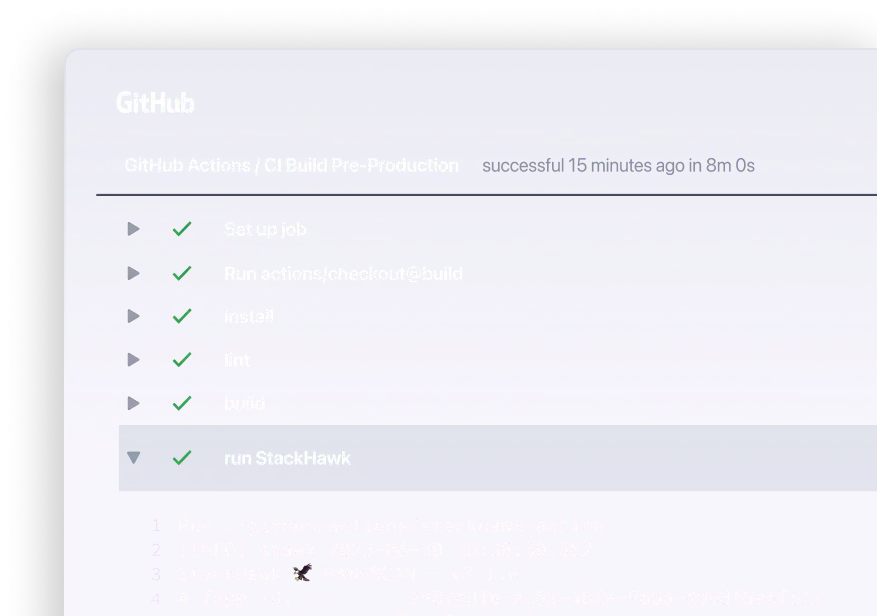
Once the environment and scope are established, the next step is to gather the necessary tools and resources. This includes selecting automated API security testing platforms like StackHawk, as well as manual testing tools like Burp Suite for more in-depth analysis. In addition to tools, it's important to ensure that your team has access to relevant documentation, such as API schemas and security policies, to effectively guide the testing process. With the right combination of tools and expertise, the security testing process can be efficient and thorough.
Proper preparation is a key factor in the success of API security testing, enabling teams to identify vulnerabilities, mitigate risks, and improve the overall security of their APIs.
Types of API Security Testing
The types of API security testing that could be performed are vast. Some are more manual, like API penetration testing, while others are more automated. When uncovering a potential API vulnerability, specific methods may be more applicable than others. For instance, if certain API security issues arise only during runtime, then it's necessary to use an API security testing tool that can evaluate the application while it's running. Meanwhile, other vulnerabilities might be detected through static analysis by using a static vulnerability scanner on the code base. With this in mind, let's take a look at a few types of API security testing tools.
Dynamic API Security Tests
While some static analysis security testing (SAST) and software composition analysis (SCA) tools have coverage for APIs, the best form of API security testing is running active (dynamic) tests against your API endpoints. This active testing is technically a form of dynamic application security testing (DAST). However, be cautious of legacy DAST tools that are not designed for API testing.
Running a dynamic API security test simulates a real API-based attack, revealing vulnerabilities stemming from both open-source dependencies and your team's code. Ideally, for the most robust API security testing, you should combine dynamic testing with SAST and SCA. However, if you're seeking an effective initial step to begin securing your APIs, dynamic testing is the recommended approach.
Static API Security Tests
Static Application Security Testing tools analyze an application's source code to pinpoint potential vulnerabilities. These tools scrutinize the code for patterns that may indicate security risks. Being language-specific, SAST tools require a match with the programming language used to write your API. To ensure effective analysis, you must select a static analysis tool that is compatible with the language of your API.
Software Composition Analysis
Software Composition Analysis tools look at the dependency tree of your application and match this against a database of known vulnerabilities. By using these tools, you would be alerted to any known vulnerabilities in libraries or frameworks that your application or API utilizes. With the ever-increasing use of open source in API development, these tools are essential to include in security testing. The limitations of SCA tools are that (1) they typically do not indicate whether a detected vulnerability is actually exploitable within your API, and (2) they focus solely on identifying vulnerabilities in open-source components, overlooking security flaws that your team might have introduced.
API Security Testing Best Practices
API security testing best practices focus on following established standards, staying updated on emerging threats, and maintaining continuous vigilance through monitoring and retesting.
Adhering to Industry Standards
To secure APIs effectively, organizations should follow established guidelines like the OWASP API Security Top 10. These standards offer a comprehensive list of common vulnerabilities, such as broken object-level authorization and improper authentication. By aligning with these guidelines, teams can implement proactive security measures and mitigate potential threats early.
Staying Updated on Evolving Threats
The API threat landscape is constantly evolving, requiring development and security teams to stay informed about new vulnerabilities and security practices. Regular updates and patches are essential to prevent attackers from exploiting known issues and to maintain robust security.
Continuous Monitoring and Retesting
API security doesn’t end with deployment. Continuous monitoring for vulnerabilities, combined with periodic retesting, ensures that newly introduced weaknesses are swiftly addressed. This ongoing vigilance is crucial in dynamic environments where APIs are frequently updated and integrated with other systems, helping organizations maintain a strong security posture over time.
Implementing Strong Authentication and Authorization
Ensuring that only authenticated and authorized users can access API resources is critical. Best practices include using OAuth or similar industry-standard protocols for managing authentication, along with role-based access control (RBAC) to enforce authorization rules.
Securing Data in Transit and at Rest
To guard against data interception or tampering, it is crucial to ensure API communication is secure by encrypting data both during transmission and while stored. Use Transport Layer Security (TLS) for encrypting API traffic, and apply encryption to sensitive data in databases, thus preventing unauthorized access.
By following these best practices, organizations can significantly reduce the risk of API vulnerabilities and ensure secure API management throughout the development lifecycle.
Essential API Security Testing Tools

API security testing relies on a mix of automated and manual tools to ensure comprehensive coverage. Automated tools, such as API security testing platforms, streamline the process by integrating into DevOps pipelines, allowing for consistent testing and faster feedback. These platforms often include capabilities for detecting common vulnerabilities and automating fixes. Notable platforms discussed in recent reviews include tools like StackHawk, Postman, and Swagger.
Manual Testing Tools
On the manual side, tools like Burp Suite offer deeper, hands-on analysis. These tools allow both security professionals and engineers to perform penetration tests, actively probing APIs for vulnerabilities that automated tools might overlook. For instance, Burp Suite is praised for its extensive features for manual testing and its ability to integrate with automated processes.
For more details, the Top 10 API Testing Tools emphasizes how integrating both automated and manual tools ensures robust API security. Additionally, Dynamic Application Security Tools and API Discovery Tools are essential for covering gaps, providing a complete toolkit for effective API testing and security management.
API Security Testing Automation with StackHawk

API security testing automation involves using tools like StackHawk to perform security testing and streamline the identification of vulnerabilities. StackHawk is designed for seamless integration into the CI/CD pipeline, making it easy to catch API security issues early in the development process. By automating the testing process, StackHawk continuously scans APIs for potential vulnerabilities, such as authentication flaws or data exposure, and provides actionable insights for developers to fix issues quickly.
Although StackHawk simplifies the security process, it is essential to complement automated testing with manual checks for complex vulnerabilities. Automated testing reduces human error, ensuring consistent, repeatable tests with every API update, which ultimately enhances the overall security posture. By using StackHawk’s automation, teams can efficiently incorporate security into their DevOps workflow and maintain a higher level of security throughout the API lifecycle.
Specialized API Security Testing Scenarios
Specialized API security testing focuses on ensuring that critical mechanisms within the API are secure, including authentication, authorization, input validation, and error handling.
Authentication and Authorization: Testing these mechanisms is essential to ensure that only legitimate users can access the API and that users have the correct permissions. Misconfigured authentication can expose sensitive data or functionality to unauthorized users.
Input Validation: Proper input validation prevents injection attacks such as SQL injection and ensures that data integrity is maintained. APIs must validate all input to prevent attackers from sending malicious data.
Error Handling: It’s crucial to test error handling to prevent information disclosure vulnerabilities. Poorly handled errors can reveal sensitive system information, which attackers can exploit to discover weaknesses in the API.
By focusing on these specialized testing scenarios, API security can be significantly strengthened, protecting critical application components from various attack vectors.
Conclusion
API security testing is crucial for protecting sensitive data and ensuring the integrity of your applications. By performing security testing, following best practices, utilizing essential tools, and incorporating automation, organizations can strengthen the security of their APIs. However, security testing is an ongoing process, requiring continuous monitoring and retesting to stay ahead of emerging threats.
To make API security testing more efficient and proactive, consider using StackHawk. StackHawk offers automated API security testing that integrates directly into your CI/CD pipeline, helping you catch vulnerabilities early. Learn more about StackHawk and start securing your APIs today.



